Remote access, Overview, Devices – BECKHOFF IPC-Security User Manual
Page 26: Software components
5. Remote Access
5.1. Overview
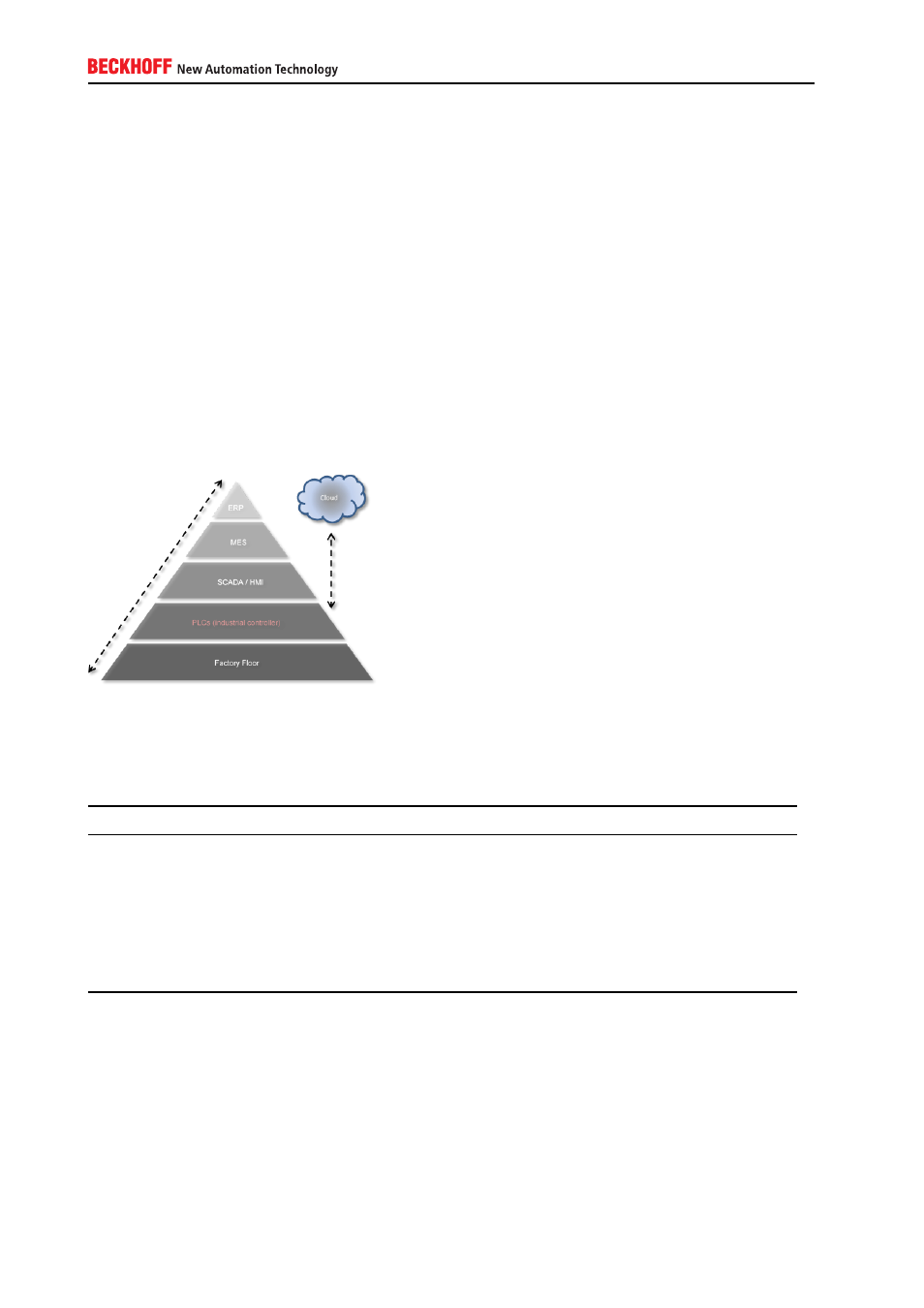
This chapter is based on the scenario that a cyber criminal tries to attack the industrial controller from a
remote location, e.g. via the local network. Network connectivity provides a cyber criminal with more ways
to compromise system security. Industrial controllers are getting more and more connected to systems that
reside in other connectivity layers, e.g. visualizations, MES systems or even the Cloud.
5.1.1. Devices
The following table provides an overview about devices that play an important part in this scenario.
Device
Category
Description
IPC/EPC
Industrial Controller
Beckhoff Industrial-/Embedded-
PC
Switch
Networking hardware
Connects devices to the network
Router
Networking hardware
Connects
different
networks
with each other
Firewall
Networking hardware
Protects networks
Modem
Networking hardware
Used for incoming/outgoing di-
alup connections
5.1.2. Software components
The following table provides an overview about software packages that play an important part in this sce-
nario.
26
