Hardening, Windows ce – BECKHOFF IPC-Security User Manual
Page 21
itself, just as this may be the case for a regular user. Please take the following chapters as a means to gain
a better awareness for this scenario.
4.1.3.1. Manipulated USB storage device
By manipulating USB storage devices, an attacker could use USB storage devices to distribute malware
which is then executed by authorized users.
Due to this, an attacker gains access to the operating system with the same privilegesas the currently logged
on user account.
4.1.3.2. Handling untrusted E-Mails
By sending out malware via E-Mail and fooling the user to believe that the content can be trusted, an attacker
could spread malware to industrial controllers and gain access to the operating system.
Due to this, an attacker gains access to the operating system with the same privileges as the currently
logged on user account.
4.2. Hardening
This chapter explains some common strategies that can be deployed to actively secure components that
are part of the scenario. Because the operating system architecture of Windows CE differs from Windows
XP, Windows 7 or Windows Embedded, each operating system family is represented by an own chapter.
4.2.1. Windows CE
4.2.1.1. Windows Updates
To apply updates on an Embedded-PC or Industrial-PC running Windows CE, Beckhoff periodically releases
new images and publishes them on its public FTP Server. Please check
ftp.beckhoff.com/software/
embpc-control/ to see if there is a new Windows CE image available for your Embedded- or Industrial-PC.
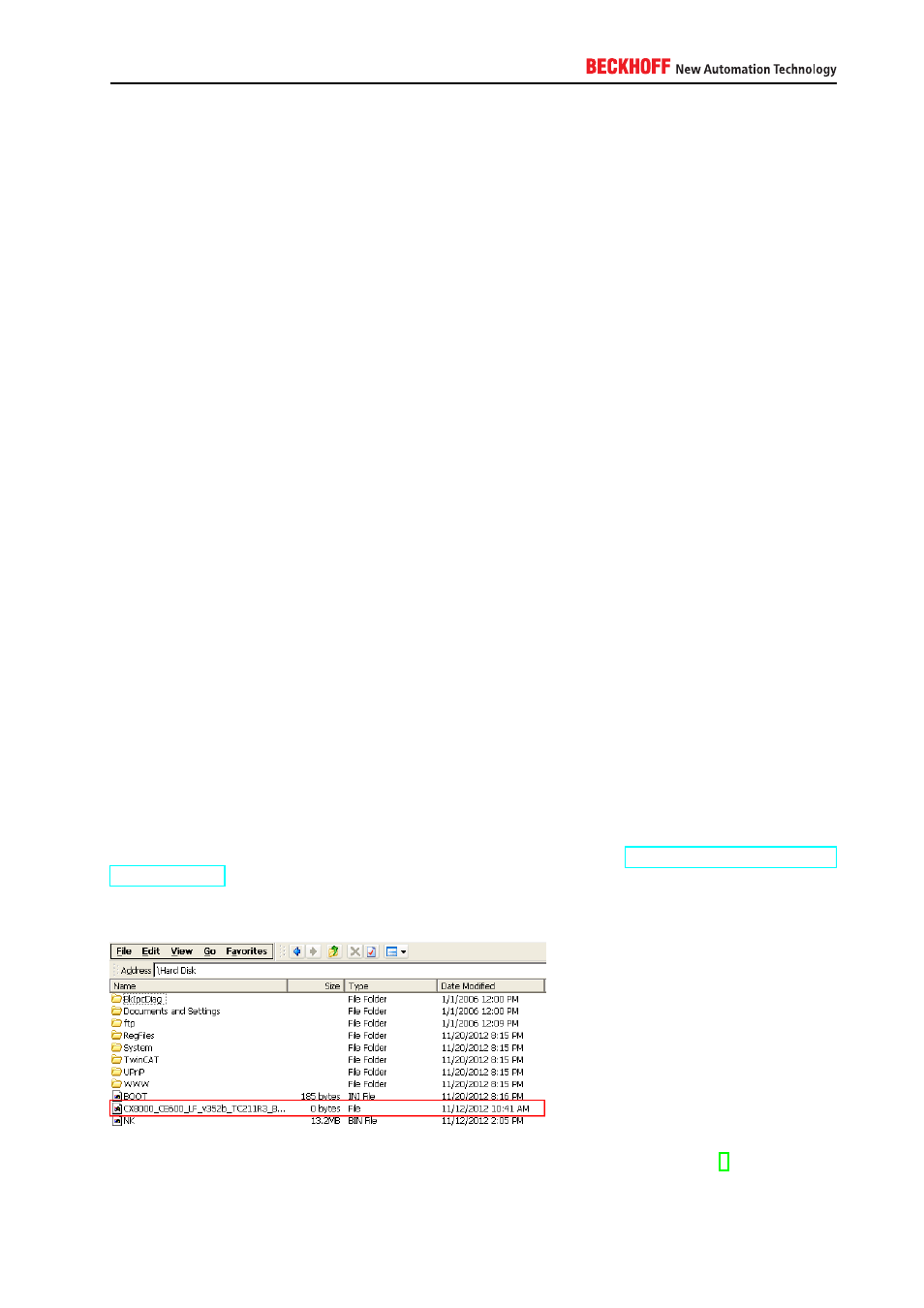
To determine the installed version simply browse to the folder \Hard Disk\. This folder contains a file that is
named after the currently installed image version.
The Beckhoff Information System provides an article about the update procedure. See [3] for more infor-
mation.
IPC Security
21
