Lancom Systems LCOS 3.50 User Manual
Page 333
̈
Chapter 14: Virtual Private Networks—VPN
LANCOM Reference Manual LCOS 3.50
333
V
irt
ua
l Pri
vat
e Ne
two
rks—
VP
N
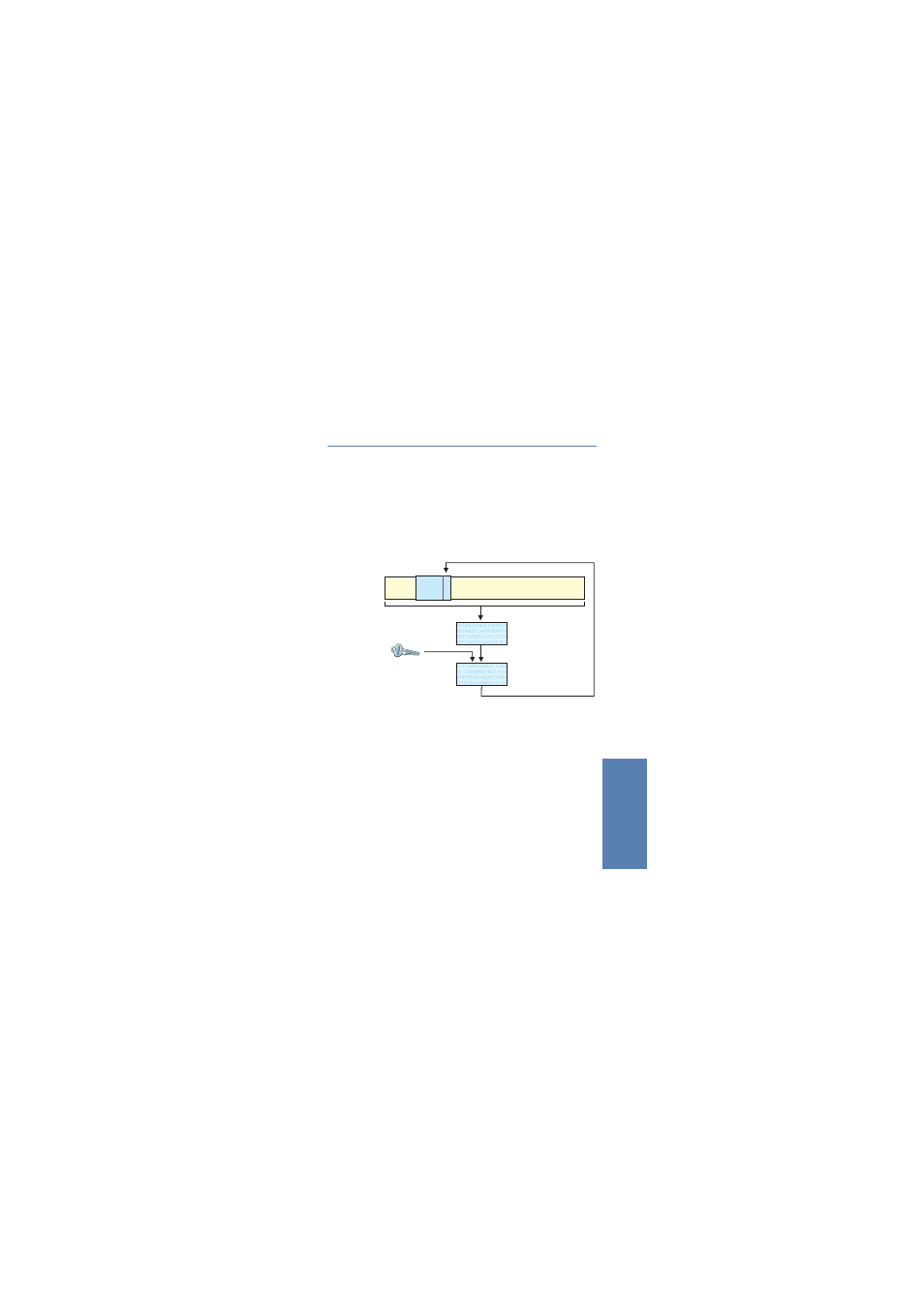
The AH process in the sender
In the sender, the authentication data is generated in 3 steps.
ቢ
A checksum is calculated for the complete package using a hash
algorithm.
ባ
This checksum is once again sent through a hash algorithm together with
a key known to both the sender and the recipient.
ቤ
This results in the required authentication data which is inserted in the AH
header.
Checking of integrity and authenticity by the recipient
The AH protocol works in a very similar manner at the recipient's end. The
recipient also uses his key to calculate the authentication data for the received
Authentication data,
ICV
Checksum
(hash code)
ቢ
ባ
ቤ
IP header
AH header
Data
ቤ
