Moxa Technologies EDS-518A Series User Manual
Page 63
EDS-518A Series User’s Manual
Featured Functions
3-48
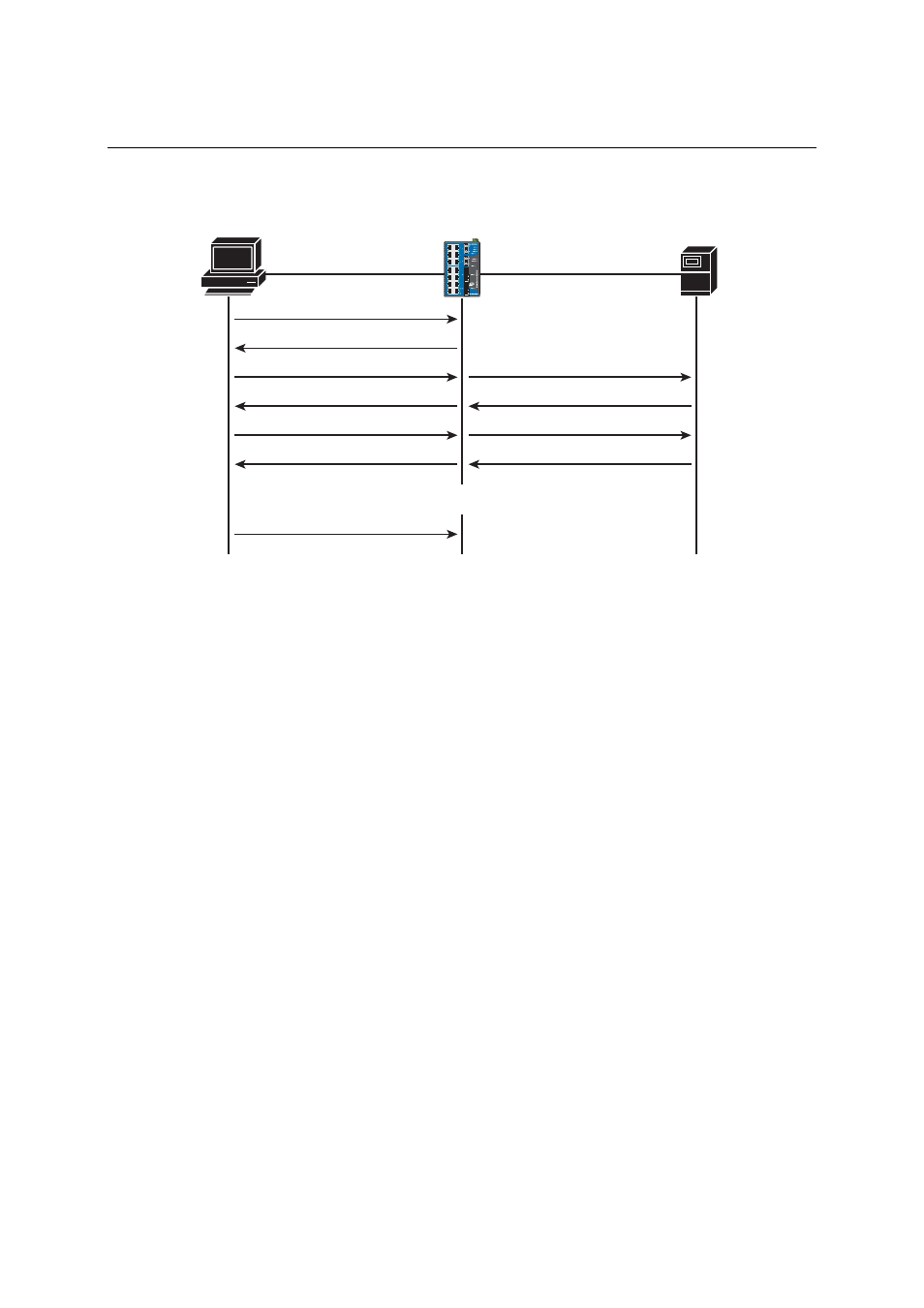
Message Exchange
Authentication
server
(RADIUS)
Client
EAPOL-Start
EAP-Request/Identity
EAP-Response/Identity
EAP-Request/OTP
EAP-Response/OTP
EAP-Success
EAPOL-Logoff
Port Authorized
Port Unauthorized
RADIUS Access-Request
RADIUS Access-Challenge
RADIUS Access-Request
RADIUS Access-Accept
1. When the supplicant receives an “EAP Request/Identity” frame, it sends an “EAP
Response/Identity” frame with its username back to the authenticator.
2. If the RADIUS server is used as the authentication server, the authenticator relays the “EAP
Response/Identity” frame from the supplicant by encapsulating it into a “RADIUS
Access-Request” frame and sends to the RADIUS server. When the authentication server
receives the frame, it looks up its database to check if the username exists. If the username is
not present, the authentication server replies with a “RADIUS Access-Reject” frame to the
authenticator if the server is a RADIUS server or just indicates failure to the authenticator if
the Local User Database is used. The authenticator sends an “EAP-Failure” frame to the
supplicant.
3. The RADIUS server sends a “RADIUS Access-Challenge,” which contains an “EAP Request”
with an authentication type to the authenticator to ask for the password from the client. RFC
2284 defines several EAP authentication types, such as “MD5-Challenge,” “One-Time
Password,” and “Generic Token Card.” Currently, only “MD5-Challenge” is supported. If the
Local User Database is used, this step is skipped.
4. The authenticator sends an “EAP Request/MD5-Challenge” frame to the supplicant. If the
RADIUS server is used, the “EAP Request/MD5-Challenge” frame is retrieved directly from
the “RADIUS Access-Challenge” frame.
5. The supplicant responds to the “EAP Request/MD5-Challenge” by sending an “EAP
Response/MD5-Challenge” frame that encapsulates the user’s password using the MD5 hash
algorithm.
6. If the RADIUS server is used as the authentication server, the authenticator relays the “EAP
Response/MD5-Challenge” frame from the supplicant by encapsulating it into a “RADIUS
Access-Request” frame along with a “Shared Secret,” which must be the same within the
authenticator and the RADIUS server, and sends the frame to the RADIUS server. The
RADIUS server checks against the password with its database, and replies with “RADIUS
Access-Accept” or “RADIUS Access-Reject” to the authenticator. If the Local User Database
is used, the password is checked against its database and indicates success or failure to the
authenticator.
