Key generation, Key establishment, Key entry and output – Enterasys Networks XSR-1805 User Manual
Page 18
IPSec session
keys
56-bit DES, 168-bit
TDES, or
128/192/256-bit
AES keys; HMAC
SHA-1 key
Established during
the Diffie-Hellman
key agreement
Stored in plaintext
in memory
Secure IPSec
traffic
Load test HMAC
SHA-1 key
≥ 80-bit HMAC
SHA-1 key
External Stored
encrypted
in NVRAM of the
real time clock
chip
Compute and verify
the HMAC SHA-1
value for the
software load test
Passwords
≥ 6-character
password
(SNMPv3 requires
at least 8
characters)
External
If stored in
configuration file,
passwords are
stored in plaintext
in Flash; if stored
in user.dat,
passwords are
stored encrypted
in Flash; Bootrom
passwords are
stored in plaintext
in NVRAM of the
real time clock
Crypto Officer
authentication for
accessing the
management
interfaces (CLI,
SNMPv3, and
Bootrom Moniot
Mode), RADIUS
authentication
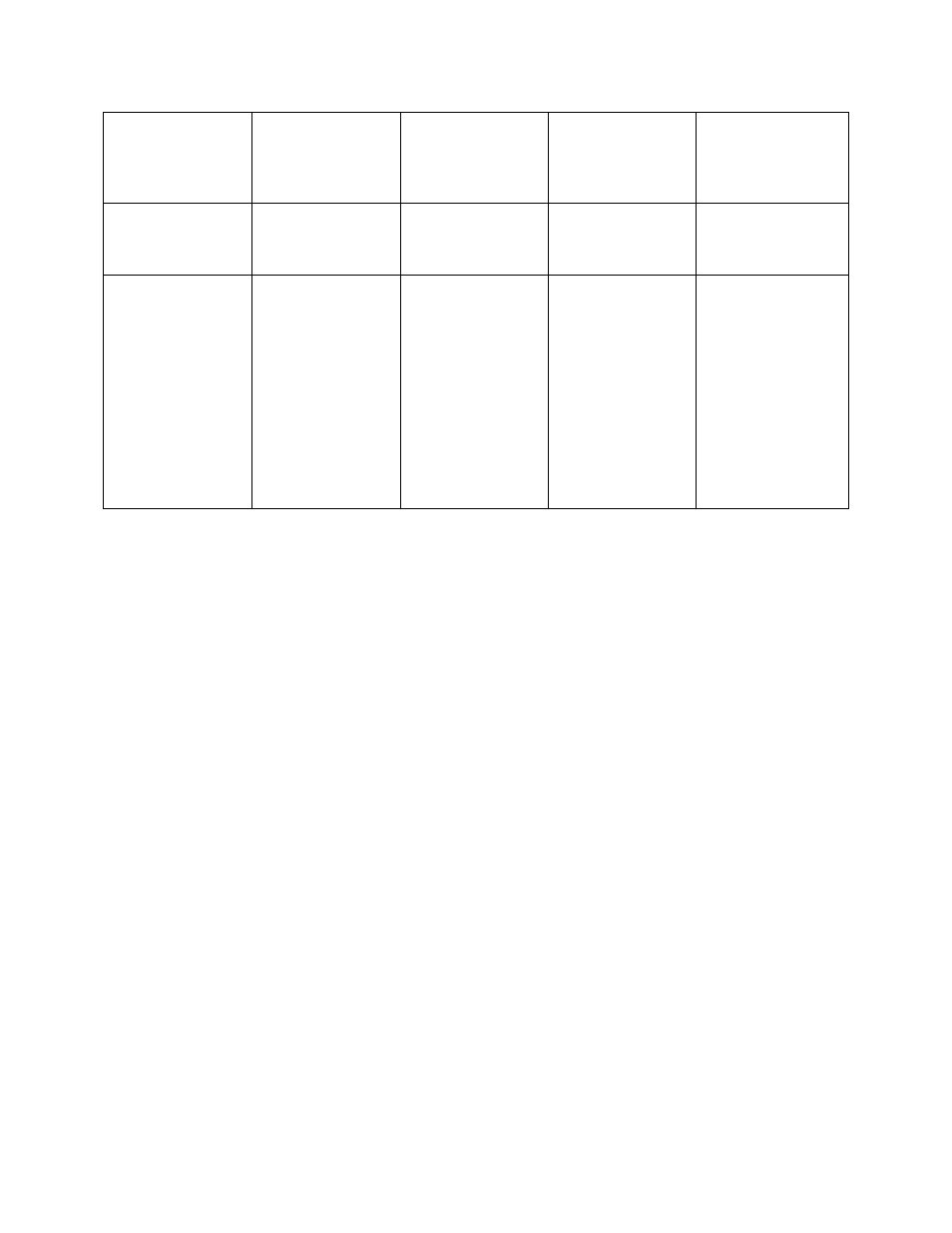
Table 8 – Listing CSPs for the Module
Key Generation
The RSA key pair used during IKE, the DSA host key pair used during
SSHv2, and the Diffie-Hellman key pairs used during IPSec and SSHv2
are all generated within the module. Additionally, each module gives the
option to generate the 3-key Triple-DES master encryption key within the
module. All keys that are generated within a module are generated using a
FIPS-approved PRNG.
Key Establishment
The modules implement SSHv2 and IKE for automatic key establishment.
These protocols implement the Diffie-Hellman key agreement to establish
shared secrets.
Key Entry and Output
© Copyright 2003
Enterasys Networks
Page 18 of 25
This document may be freely reproduced and distributed whole and intact including this Copyright Notice.
Three types of secret keys can be entered in plaintext form into the
modules: the master encryption key, pre-shared keys, and the load test
HMAC SHA-1 key. The master encryption key can either be specified or
generated within the module. Pre-shared keys, if chosen as the
authentication method for IKE, must always be entered into the module by
the Crypto Officer. The HMAC SHA-1 key must be entered into the
module before a valid software file is loaded into the module.
The three keys are entered electronically if the SSH or the Telnet over
IPSec secured remote session is used or manually if the module is
accessed locally through the console port. When these keys are manually
entered, a manual key entry test is performed.
