Cryptographic key management, Ryptographic, Anagement – Enterasys Networks XSR-1805 User Manual
Page 16
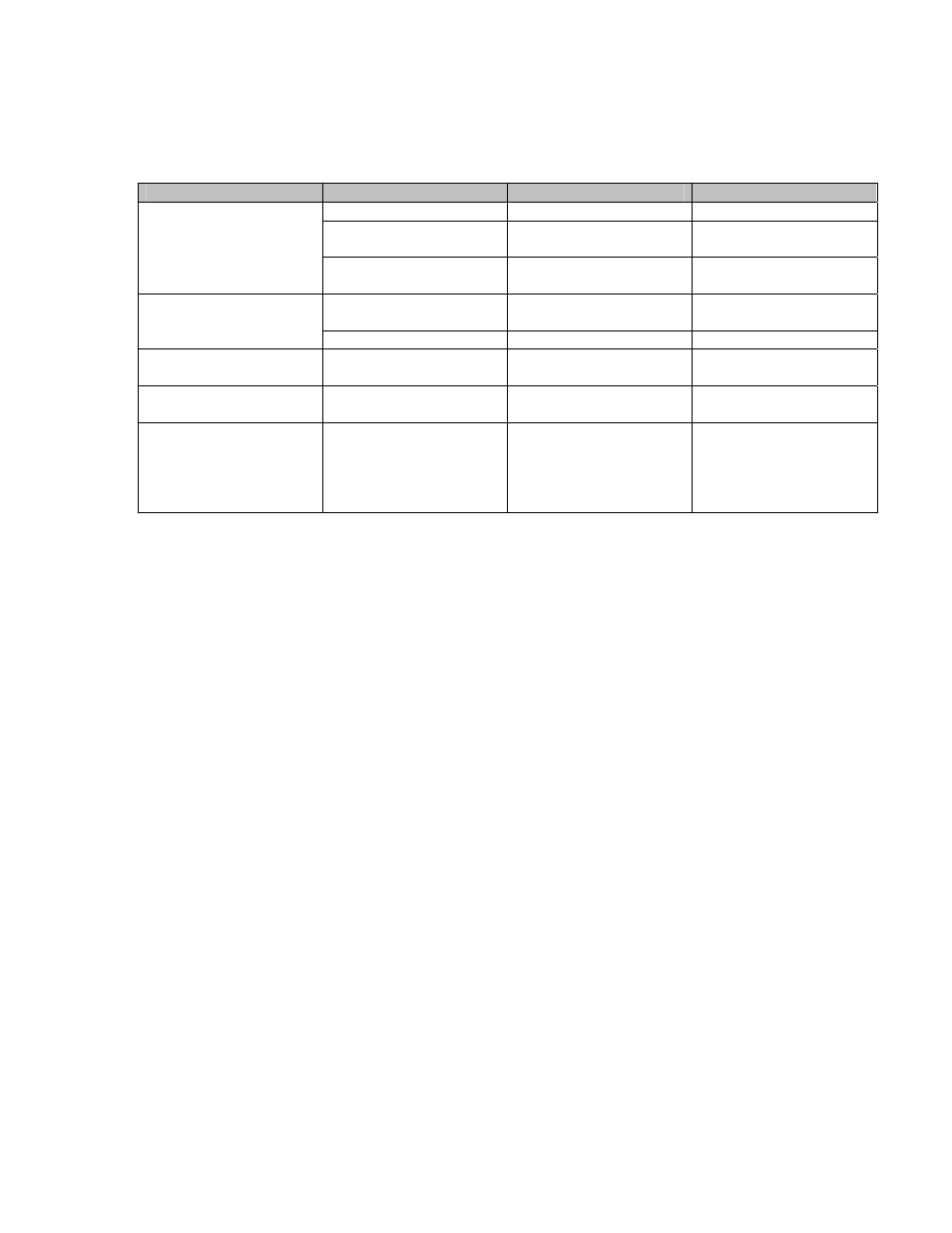
Cryptographic Key Management
The modules implement the following FIPS-approved algorithms:
Type
Algorithm
Standard
Certificate Number
AES (CBC)
FIPS 197
Cert. #48, #106, #107
Triple-DES (CBC and
ECB)
FIPS 46-3
Cert. #158, #218, #219,
#220
Symmetric
DES (CBC)
FIPS 46-3
Cert. #204, #238, #239,
#240
DSA
FIPS 186-2 Change
Notice 1
Cert. #97
Asymmetric
RSA Digital Signature
PKCS #1
Vendor affirmed
Hash function
SHA-1
FIPS 180-1
Cert. #143, #197, #198,
#199
MAC
HMAC SHA-1
FIPS 198
Cert. #143, #197, #198,
#199; vendor affirmed
PRNG Appendix
3.1
(Algorithm
1) for computing DSA
keys
Appendix 3.1 for
general purpose
FIPS 186-2 Change
Notice 1
N/A
Table 7 – FIPS-Approved Algorithm supported by the Module
Note: DES should be used for legacy purposes only.
The modules implement the following non-FIPS-approved algorithms:
• HMAC MD5
• MD5
• MD4
• 40-bit and 128-bit RC4
• CAST
• Blowfish
• Twofish
• ARCfour
• Diffie-Hellman (permitted for use in a FIPS-approved mode of
operation)
Cryptographic algorithms are implemented in software and in hardware by
© Copyright 2003
Enterasys Networks
Page 16 of 25
This document may be freely reproduced and distributed whole and intact including this Copyright Notice.
