Enterasys Networks XSR-1805 User Manual
Page 17
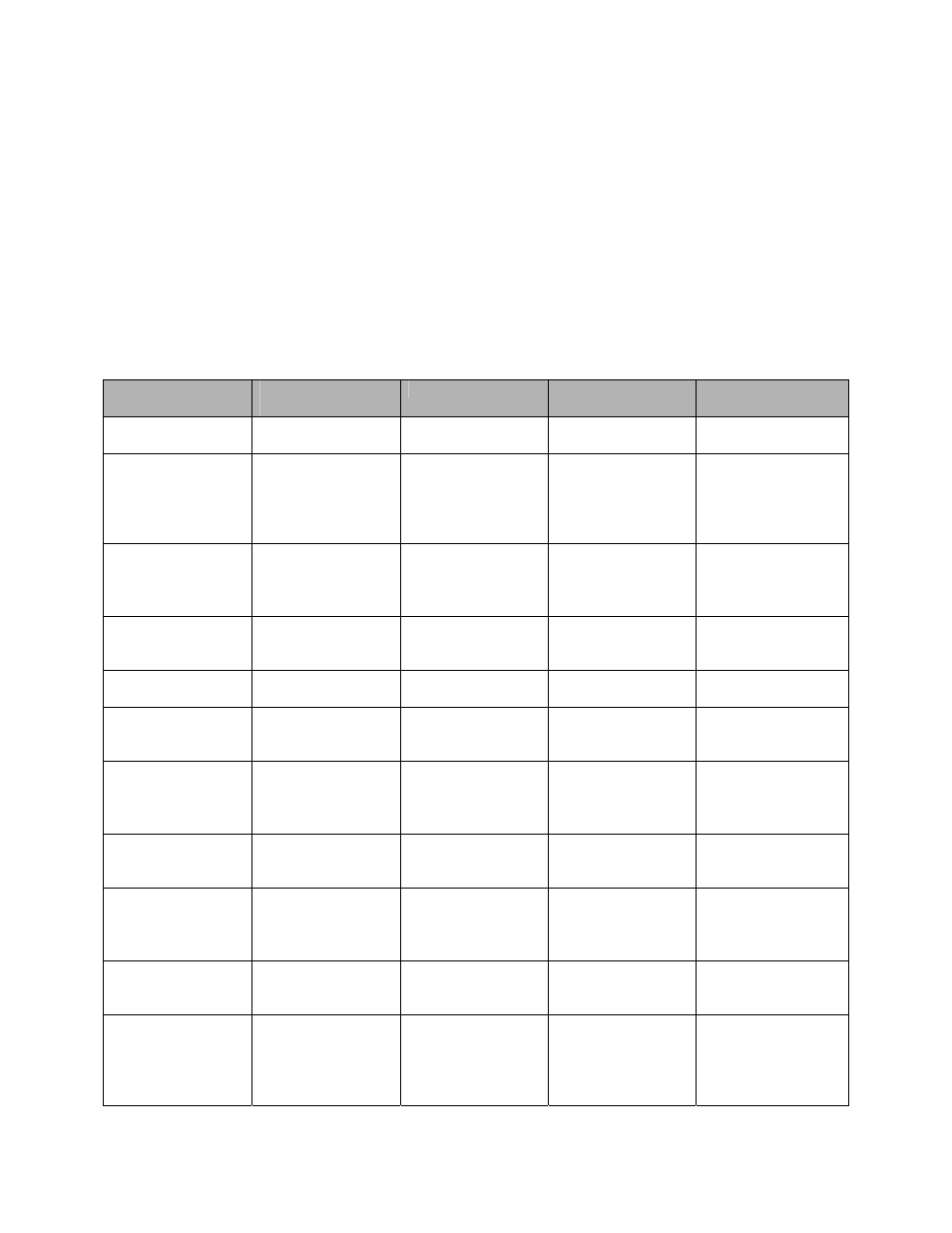
the encryption accelerators. The encryption accelerators implement the
following FIPS-approved algorithms:
• XSR-18xx – Triple-DES, DES, and HMAC SHA-1
• XSR-3250 – AES, Triple-DES, DES, and HMAC SHA-1
Cryptographic processing is performed during SSHv2, SNMPv3, IKE,
IPSec, and when accessing and storing database files.
The module supports the following critical and non-critical security
parameters:
CSPs and non-
critical SPs
CSPs and non-
critical SPs type
Generation
Storage
Use
Key encryption
key
168-bit TDES key
External
Hard-coded in
plaintext
Encrypts master
encryption key
Master encryption
key
168-bit TDES key
Internal – using
FIPS 186-2 PRNG
Or
External
Stored encrypted
in NVRAM of the
Dallas DS1687
real time clock
chip
Encrypts user data,
certificates, and
DSA host key, and
the load test HMAC
SHA-1 key
DSA host key pair
160-bit DSA
private key and
1024-bit DSA
public key
Internal – using
FIPS 186-2 PRNG
Stored encrypted
in Flash
Module
authentication
during SSHv2
IKE RSA key pair
1024-bit RSA
private/public key
pair
Internal – using
FIPS 186-2 PRNG
Stored encrypted
in Flash
Module
authentication
during IKE
IKE User RSA
public keys
1024-bit RSA
public key
External Stored
encrypted
in Flash
User authentication
during IKE
Pre-shared keys
≥ 6-character pre-
shared key
External Stored
encrypted
in Flash
User and module
authentication
during IKE
IKE Diffie-Hellman
key pair
768/1024/1536-bit
Diffie-Hellman
private/public key
pair
Internal – using
FIPS 186-2 PRNG
Stored in plaintext
in memory
Key agreement
during IKE
IKE User Diffie-
Hellman public key
768/1024/1536-bit
Diffie-Hellman
public key
External
Stored in plaintext
in memory
Key agreement
during IKE
SSHv2 Diffie-
Hellman key pair
768/1024/1536-bit
Diffie-Hellman
private/public key
pair
Internal – using
FIPS 186-2 PRNG
Stored in plaintext
in memory
Key agreement
during SSHv2
SSHv2 User Diffie-
Hellman public key
768/1024/1536-bit
Diffie-Hellman
public key
External
Stored in plaintext
in memory
Key agreement
during SSHv2
SSHv2 session
keys
168-bit TDES or
128/192/256-bit
AES keys; HMAC
SHA-1 keys
Established during
the SSH key
exchange using
the Diffie-Hellman
key agreement
Stored in plaintext
in memory
Secure SSH traffic
© Copyright 2003
Enterasys Networks
Page 17 of 25
This document may be freely reproduced and distributed whole and intact including this Copyright Notice.
