Security zone management configuration, Security zone management overview – H3C Technologies H3C SecBlade FW Cards User Manual
Page 2
1
Security zone management configuration
Security zone management overview
Traditional firewall policies are configured based on packet inbound and outbound interfaces on early
dual-homed firewalls. With the development of firewalls, they can not only connect the internal and
external network, but also connect the internal network, external network, and the Demilitarized Zone
(DMZ). Also, they are providing high-density ports. A high-end firewall can provide dozens of physical
interfaces to connect multiple logical subnets. In this networking environment, traditional interface-based
policy configuration mode requires configuration of a security policy for each interface, which brings
great working loads for administrators and thus increases probability for introducing security problems
due to improper configurations.
The industry-leading firewalls solve the above problems by implementing security policies based on
security zones. A security zone is an abstract conception. It can include physical interfaces and logical
interfaces, and also Trunk interface + VLAN. Interfaces added to the same security zone have consistent
security needs. Therefore, an administrator can classify interfaces (assign them to different zones) based
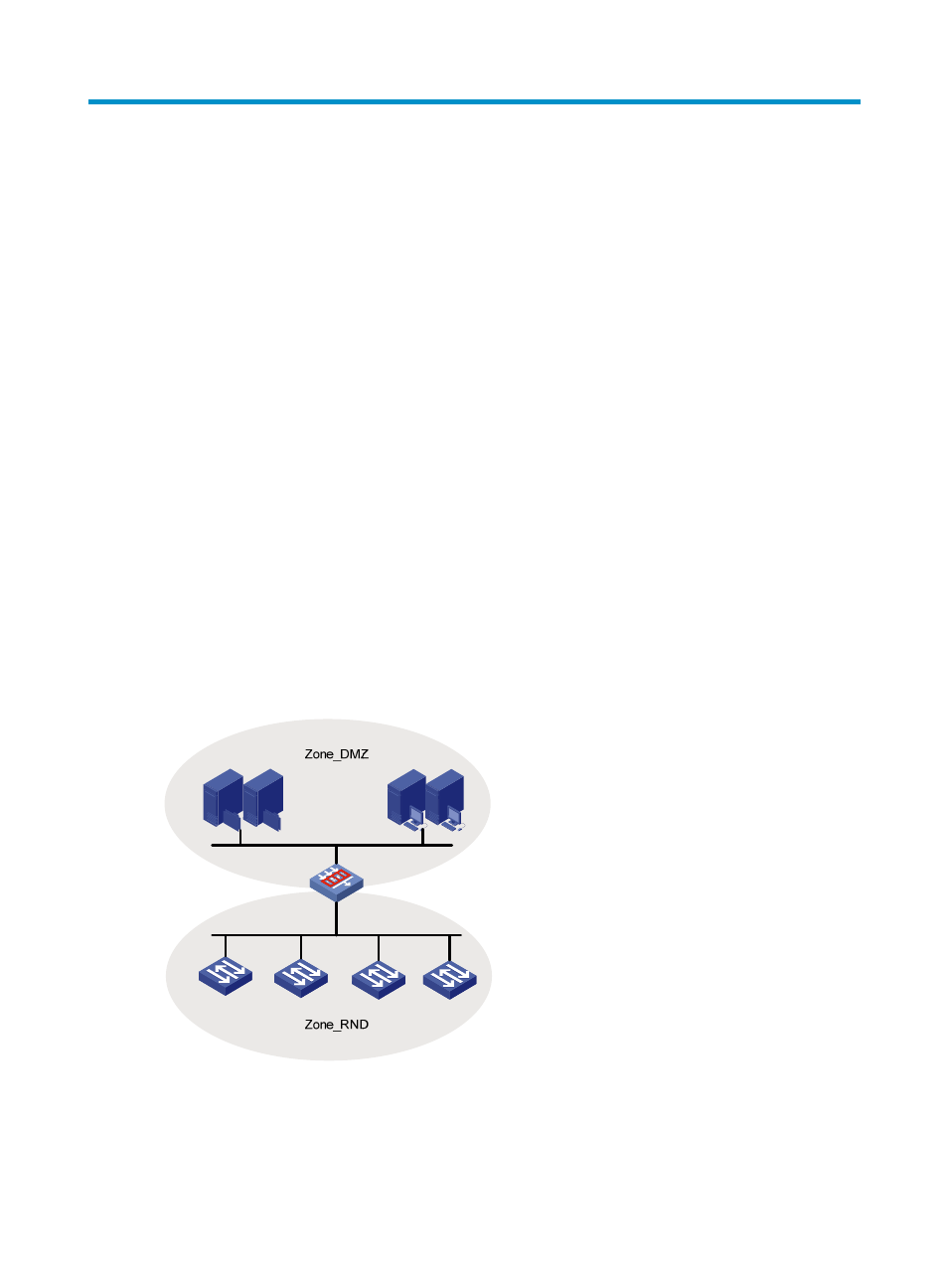
on their security needs, thus implementing hierarchical policy management. For example, on the firewall
in the following figure, the administrator can add the interface that connects the R&D area to Zone_RND,
and the interface connecting the servers to Zone_DMZ. In this way, the administrator only needs to
deploy security policies in the two zones. If the network changes in the future, the administrator only
needs to adjust the interfaces in a certain zone, without modifying the security policies. The security zone
management feature not only simplifies policy maintenance but also separates network services from
security services.
Figure 1 Security zone classification
