Zilog EZ80F91AZA User Manual
Page 17
UM020107-1211
SSL Handshake Protocols
ZTP Network Security SSL Plug-In
User Manual
11
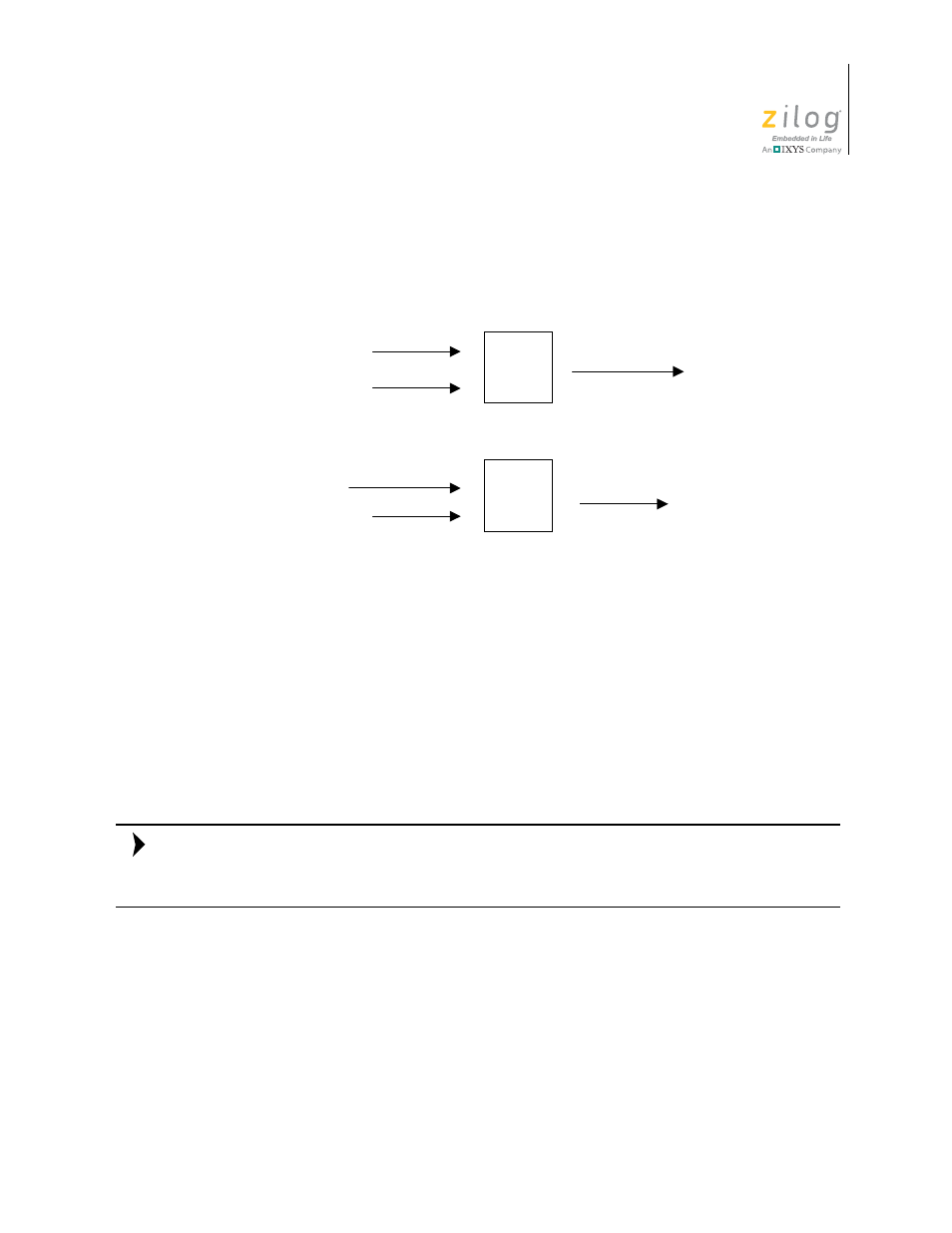
involved before encrypted data transfer occurs. Figure 3 displays the typical flow of asym-
metric cipher encryption and decryption.
In the context of SSL, the server possesses a private key which is not distributed or shared
with any client. The corresponding public key is contained in the server’s X.509 certificate
and freely distributed to prospective clients when they initiate a new SSL session. There-
fore, unlike symmetric ciphers, there is no risk associated with a public key being compro-
mised by a client because the public key is not a secret.
The disadvantage of asymmetric ciphers is that they are more computationally intensive
than symmetric ciphers. As a result, asymmetric ciphers run much slower than symmetric
algorithms. The difference in performance can be a few orders of magnitude, increasing as
key strength is increased.
The SSL protocol uses an asymmetric cipher (key exchange algorithm) to exchange the
Master Key, and it uses a symmetric cipher to encrypt/decrypt the upper layer data blocks
when an SSL session is established.
Stream Cipher.
A stream cipher is a symmetric cipher that operates on an arbitrary-sized
input message to produce an output message of the same length. The algorithm expands a
cryptographic key into a key stream in which its length matches the length of the input
text. The input text and key stream are exclusively ORed to produce the final cipher text
output message.
Block Cipher.
A block cipher is a symmetric cipher that breaks an input message into
fixed-sized blocks. Padding may be required to ensure that the input text is an exact multi-
Figure 3. Asymmetric Cipher Encryption and Decryption
Cipher
Plain Text
Public Key
Encrypted Text
Cipher
Plain Text
Private Key
Encrypted Text
Asymmetric Cipher Encryption
Asymmetric Cipher Decryption
Note:
