Zilog EZ80F91AZA User Manual
Page 16
UM020107-1211
SSL Handshake Protocols
ZTP Network Security SSL Plug-In
User Manual
10
Cipher.
A cipher is an algorithm that transforms plain text into encrypted text, and vice
versa. In terms of security, ciphers are used to provide privacy. Even if an encrypted mes-
sage is intercepted, the plain text content of the message is not visible, and therefore the
communication between endpoints is maintained as private.
Cipher algorithms require a special input called a key to encrypt/decrypt data. This key is
used to uniquely scramble the data as it passes through the cipher algorithm. Cryptograph-
ically-strong ciphers are capable of producing very different output blocks for a given
plain text block if only a few bits in the key are modified. In general, the longer the key (in
bits) the harder it is to determine a plain text message from examining its cipher output.
Ciphers are broadly classified as:
•
Symmetric ciphers
•
Asymmetric ciphers
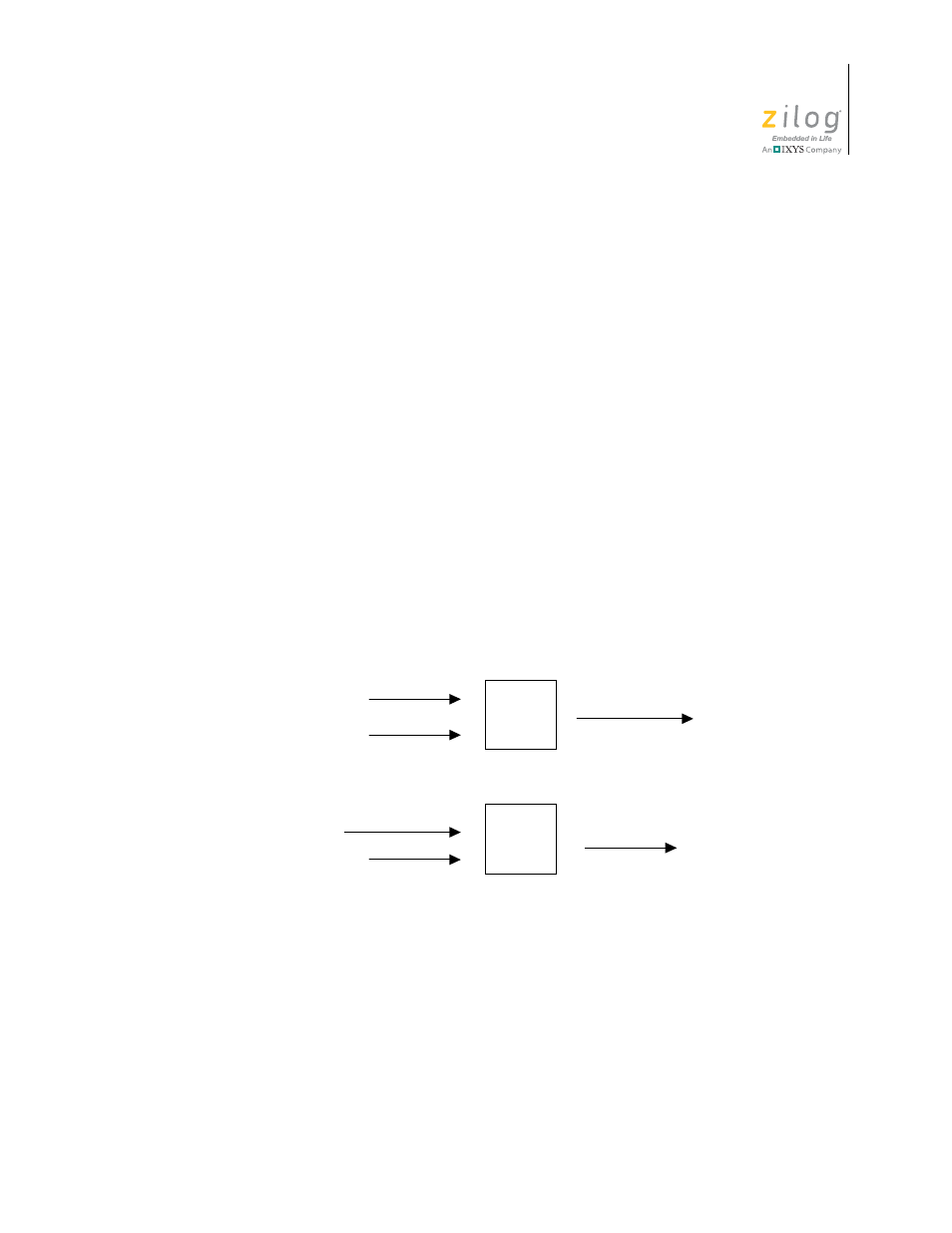
Symmetric Ciphers.
A symmetric cipher uses the same shared key to encrypt and decrypt
a message. Therefore, before a symmetric cipher is used to transfer encrypted data, it is
necessary for both parties to possess the same secret key. Figure 2 displays the typical
flow of symmetric cipher encryption and decryption.
One of the challenges with symmetric algorithms is to maintain the shared secret as truly
secret. For example, if there are 100 clients that communicate with a particular server
using a shared secret and this secret is compromised by one of the clients, then all 101 sys-
tems must be updated with a new shared secret.
Asymmetric Ciphers.
Asymmetric algorithms use different keys to encrypt and decrypt
data. Asymmetric algorithms typically use a public and private key pair. Therefore, unlike
symmetric algorithms, it is not necessary to distribute a shared secret to all parties
Figure 2. Symmetric Cipher Encryption and Decryption
Cipher
Plain Text
Shared Key
Encrypted Text
Cipher
Plain Text
Shared Key
Encrypted Text
Symmetric Cipher Encryption
Symmetric Cipher Decryption
