SilentKnight System IP traffic patterns and network integration highlights User Manual
Page 5
4
Scenario 2: IPDACT and VisorALARM in a VPN
The Teldat IP alarm system already offers high protection and secured data transmission. The payload of
the UDP traffic exchanged between the IPDACT and the VisorALARM is encrypted in AES-512, but also
the system offers its own protection mechanism for device substitution and man-in-the-middle attacks. As
such, the implementation of a VPN network for this system is not necessary. However, if a VPN network is
already available, the user can seamlessly integrate his IPDACTC’s and VisorALARM’s, just as he
integrates other third party or generic hosts, with no additional precautions.
Typical VPN implementations consist on establishing a tunnel between the subscriber’s and the ARC
gateways along the Internet. Figure 2 depicts a simple scenario where the subscriber’s and ARC default
gateways are also terminating the VPN tunnel at their respective sides:
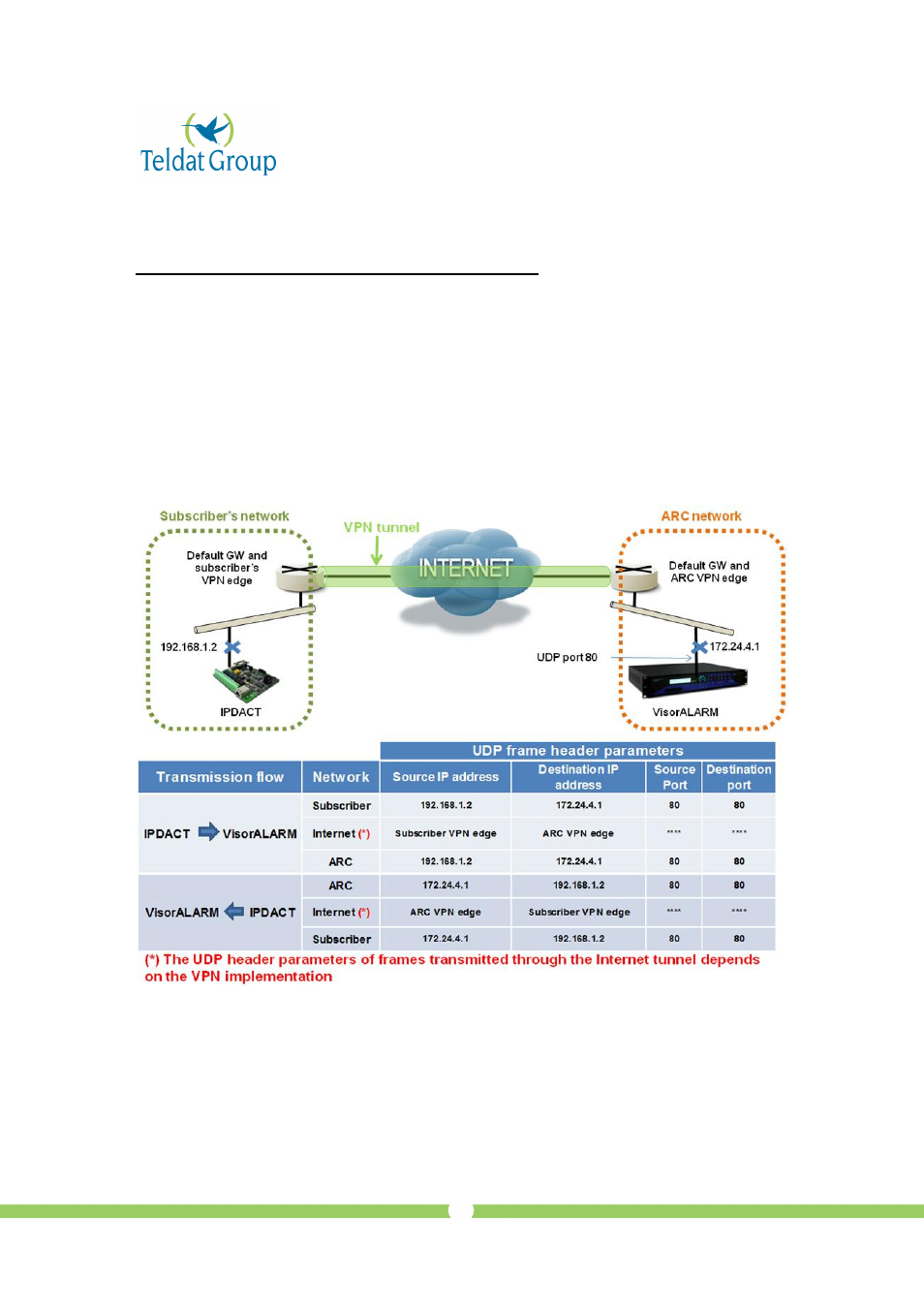
Figure 2. VPN scenario and UDP frame header parameters.
VPN implementation based on IP tunnels provides the user with LAN-to-LAN “transparency”: Some hosts
in the subscriber’s LAN network (those ones defined in the Security Policy) will have direct IP
connectivity to hosts and servers in the ARC LAN network. For the host (IPDACT) “sees” its remote peer
(VisorALARM) as if it was connected to the same IP network.
In the Figure 2 example, the subscriber’s VPN edge gateway should be capable of route the IP traffic
destined to host 172.24.4.1 through the VPN tunnel. The ARC VPN gateway should include a route to the
host at 192.168.1.2 through the VPN tunnel.
