Dos attack protection, Smurf attacks, Chapter 10 – Brocade Communications Systems Brocade ICX 6650 6650 User Manual
Page 287: Chapter
Brocade ICX 6650 Security Configuration Guide
267
53-1002601-01
Chapter
10
DoS Attack Protection
lists DoS protection features supported in Brocade ICX 6650. These features are
supported in the Layer 2, base Layer 3, edge Layer 3, and full Layer 3 software images, except
where noted.
This chapter explains how to protect your Brocade devices from Denial of Service (DoS) attacks.
In a Denial of Service (DoS) attack, a device is flooded with useless packets, hindering normal
operation.Brocade devices include measures for defending against two types of DoS attacks Smurf
attacks and TCP SYN attacks.
Smurf attacks
A Smurf attack is a kind of DoS attack in which an attacker causes a victim to be flooded with
Internet Control Message Protocol (ICMP) echo (Ping) replies sent from another network.
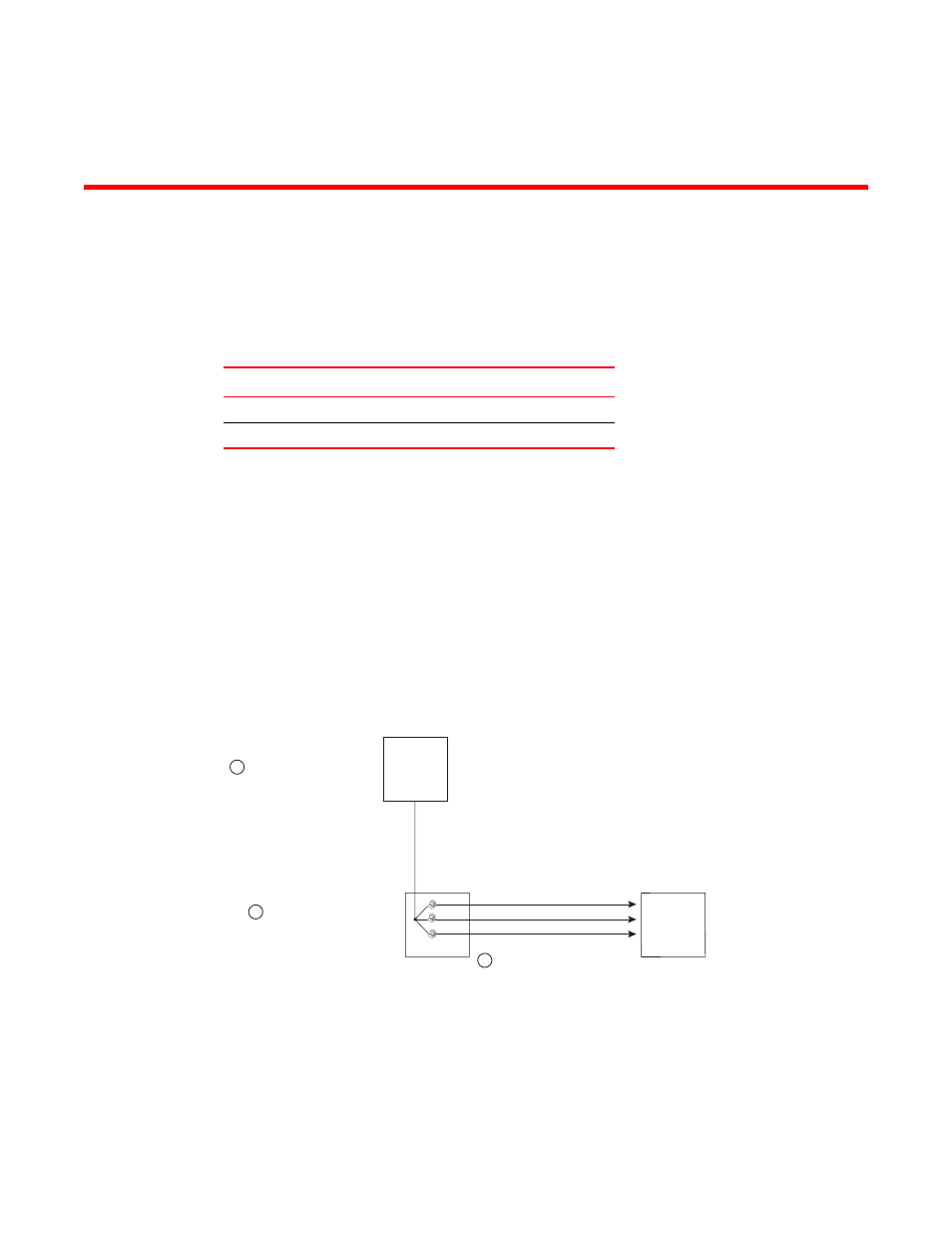
illustrates how a Smurf attack works.
FIGURE 14
How a Smurf attack floods a victim with ICMP replies
The attacker sends an ICMP echo request packet to the broadcast address of an intermediary
network. The ICMP echo request packet contains the spoofed address of a victim network as its
source. When the ICMP echo request reaches the intermediary network, it is converted to a Layer 2
broadcast and sent to the hosts on the intermediary network. The hosts on the intermediary
network then send ICMP replies to the victim network.
TABLE 64
Supported DoS protection features
Feature
Brocade ICX 6650
Smurf attack (ICMP attack) protection
Yes
TCP SYN attack protection
Yes
2
1
3
Attacker
Intermediary
Victim
Attacker sends ICMP echo requests to
broadcast address on Intermediary’s
network, spoofing Victim’s IP address
as the source
If Intermediary has directed broadcast
forwarding enabled, ICPM echo requests
are broadcast to hosts on Intermediary’s
network
The hosts on Intermediary’s network
send replies to Victim, inundating Victim
with ICPM packets
