Axis Communications Video Server 243Q Blade User Manual
Page 40
40
AXIS 243Q Blade - System options
To perform the authentication, the RADIUS server uses various EAP methods/protocols.
The one used in the Axis implementation is EAP-TLS (EAP-Transport Layer Security).
The AXIS network video device presents its certificate to the network switch, which in turn
forwards this to the RADIUS server. The RADIUS server validates or rejects the certificate
and responds to the switch, and sends its own certificate to the client for validation. The
switch then allows or denies network access accordingly, on a preconfigured port.
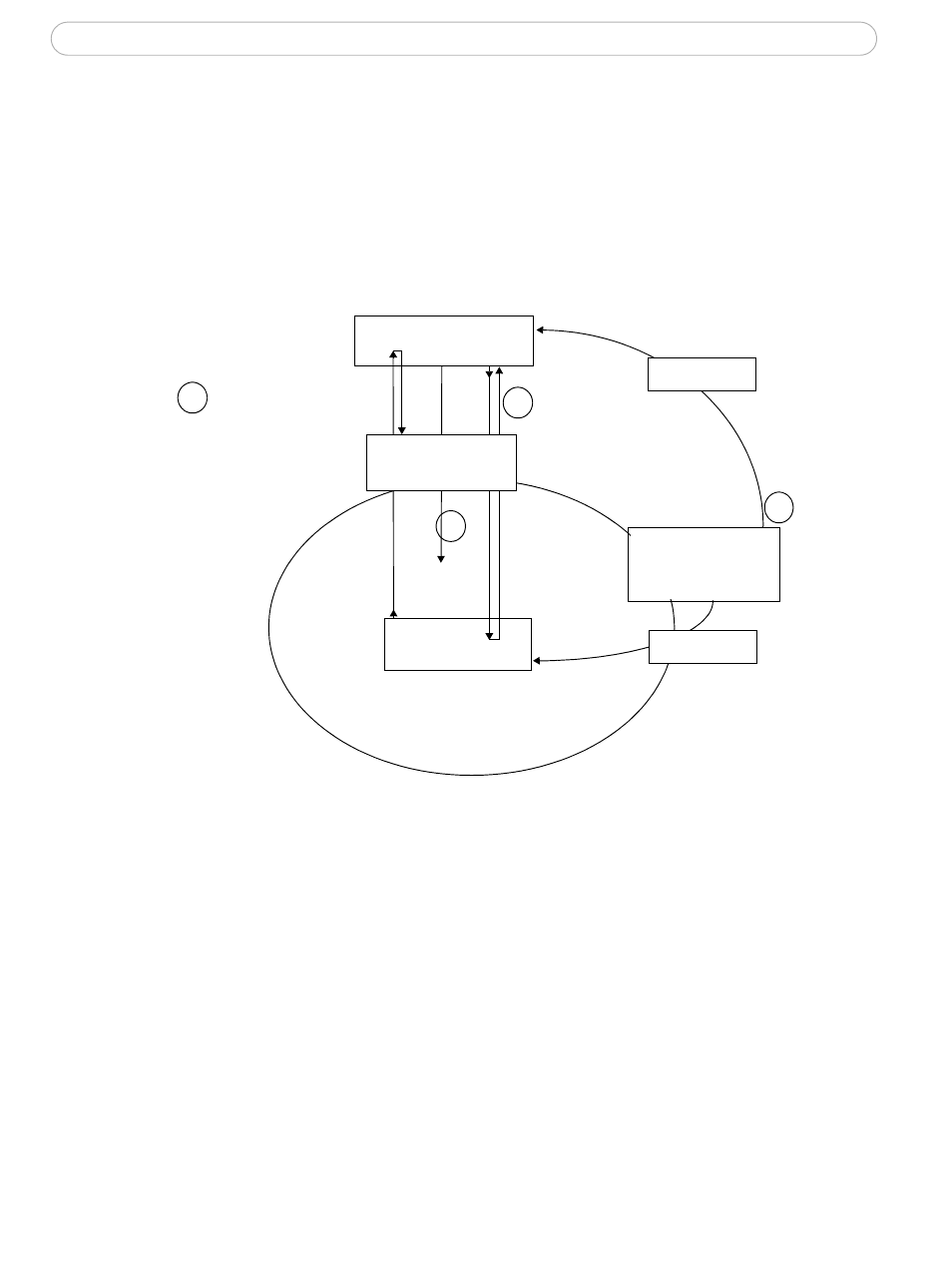
The authentication process
RADIUS
RADIUS (Remote Authentication Dial In User Service) is an AAA (Authentication,
Authorization and Accounting) protocol for applications such as network access or IP
mobility. It is intended to work in both local and roaming situations.
Protected network
Axis video device
Q: Certificate OK?
Certificate
Authority (CA)
3
1
2
4
A: OK
RADIUS
server
Network
switch
Q: Certificate OK?
A: OK
Certificate
Certificate
1. A CA server provides the required signed certificates.
2. The Axis video device requests access to the protected network at the network switch.
The switch forwards the video device’s CA certificate to the RADIUS server, which then
replies to the switch.
3. The switch forwards the RADIUS server’s CA certificate to the video device, which
also replies to the switch.
4. The switch keeps track of all responses to the validation requests. If all certificates are
validated, the Axis video device is allowed access to the protected network via a
preconfigured port.
