Abridged data sheet, Network function commands – Rainbow Electronics MAX66140 User Manual
Page 13
MAX66140
ISO 15693-Compliant Secure Memory
______________________________________________________________________________________
15
Request Flags, Inventory_flag Bit Set
Bits 8, 7, and 4: No Function
These bits have no function. They must be transmitted as 0.
Bit 6: Slot Counter Flag (Nb_slots_flag)
This bit specifies whether the command is processed using a slot counter (bit = 0) or without using the slot counter
(bit = 1).
Bit 5: Application Family Identifier Flag (AFI_flag)
To detect only slaves with a certain AFI value, the AFI_flag bit must be 1 and the desired AFI value must be included
in the request. If the least significant nibble of the AFI in the request is 0000b, slaves process the command only if
the most significant nibble of the AFI matches. If the AFI in the request is 00h, all slaves process the command
regardless of their AFI.
Bit 3: Inventory Flag (Inventory_flag)
This bit must be 1 for the Inventory command only. For all other commands, this bit must be 0.
Bit 2: Data Rate Flag (Data_rate_flag)
This bit specifies whether the response data packet is transmitted using the low data rate (bit = 0) or the high data
rate (bit = 1).
Bit 1: Subcarrier Flag (Subcarrier_flag)
This bit specifies whether the response data packet is transmitted using a single subcarrier (bit = 0) or two subcarri-
ers (bit = 1).
Network Function Commands
The command descriptions show the data fields of the request and response data packets. To create the complete
frame, an SOF, 16-bit CRC, and EOF must be added (see Figure 5). The ISO 15693 standard defines four network
function commands: Inventory, Stay Quiet, Select, and Reset to Ready. This section describes the format of the
request and response data packets.
Inventory
This command allows the master to learn the UIDs and DSFIDs of all slaves in its RF field in an iterative process. It is
the only command for which the Inventory_flag bit must be 1. The Inventory command uses two command-specific
parameters, which are the mask length and the mask pattern. The mask allows the master to preselect slaves for
responding to the Inventory command. The LSb of the mask aligns with the LSb of the slave’s UID. The master can
choose not to use a mask, in which case all slaves qualify, provided they are not excluded by the AFI criteria (see
the
Request Flags
section). The maximum mask length is 60 (3Ch, if Nb_slots_flag = 0) or 64 (40h, if Nb_slots_flag =
1). The mask pattern defines the least significant bits (as many as specified by the mask length) that a slave’s UID
must match to qualify for responding to the Inventory command (case Nb_slots_flag = 1). If the slot counter is used
(Nb_slots_flag = 0), the value of the slot counter extends the mask pattern at the higher bits for comparison to the
slave’s UID. The slot counter starts at 0 after the inventory request frame is transmitted and increments during the
course of the Inventory command with every subsequent EOF sent by the master. The processing of an Inventory
command ends when the master sends the SOF of a new frame.
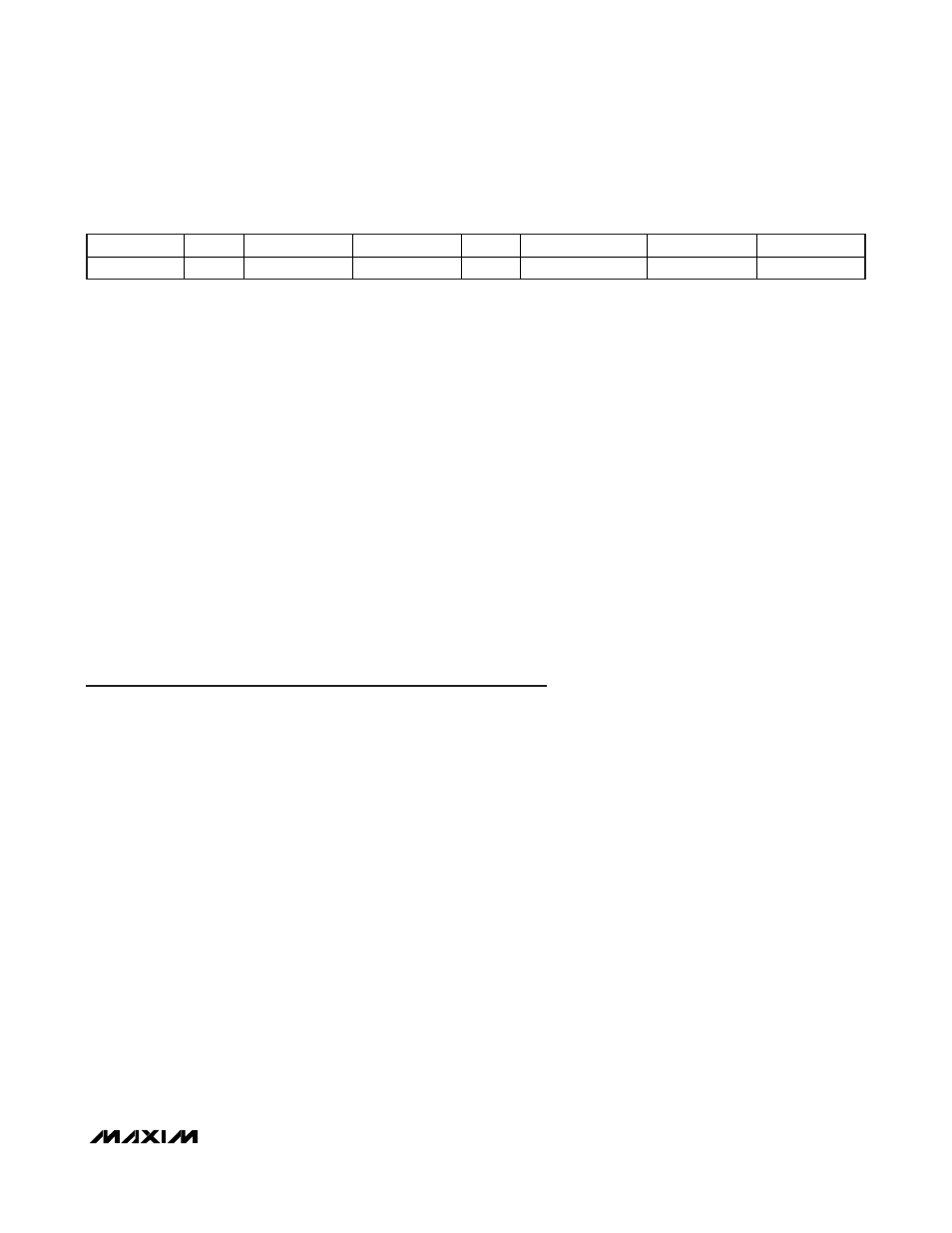
BIT 8 (MS)
BIT 7
BIT 6
BIT 5
BIT 4
BIT 3
BIT 2
BIT 1 (LS)
0 0
Nb_slots_flag
AFI_flag
0
Inventory_flag
(=
1)
Data_rate_flag
Subcarrier_flag
ABRIDGED DATA SHEET
