Dynamic wep key exchange – ZyXEL Communications NWD-270N User Manual
Page 79
Appendix C Wireless LANs
NWD-270N User’s Guide
79
PEAP (Protected EAP)
Like EAP-TTLS, server-side certificate authentication is used to establish a secure connection,
then use simple username and password methods through the secured connection to
authenticate the clients, thus hiding client identity. However, PEAP only supports EAP
methods, such as EAP-MD5, EAP-MSCHAPv2 and EAP-GTC (EAP-Generic Token Card),
for client authentication. EAP-GTC is implemented only by Cisco.
LEAP
LEAP (Lightweight Extensible Authentication Protocol) is a Cisco implementation of IEEE
802.1x.
Dynamic WEP Key Exchange
The AP maps a unique key that is generated with the RADIUS server. This key expires when
the wireless connection times out, disconnects or reauthentication times out. A new WEP key
is generated each time reauthentication is performed.
If this feature is enabled, it is not necessary to configure a default encryption key in the
wireless security configuration screen. You may still configure and store keys, but they will
not be used while dynamic WEP is enabled.
"
EAP-MD5 cannot be used with Dynamic WEP Key Exchange
For added security, certificate-based authentications (EAP-TLS, EAP-TTLS and PEAP) use
dynamic keys for data encryption. They are often deployed in corporate environments, but for
public deployment, a simple user name and password pair is more practical. The following
table is a comparison of the features of authentication types.
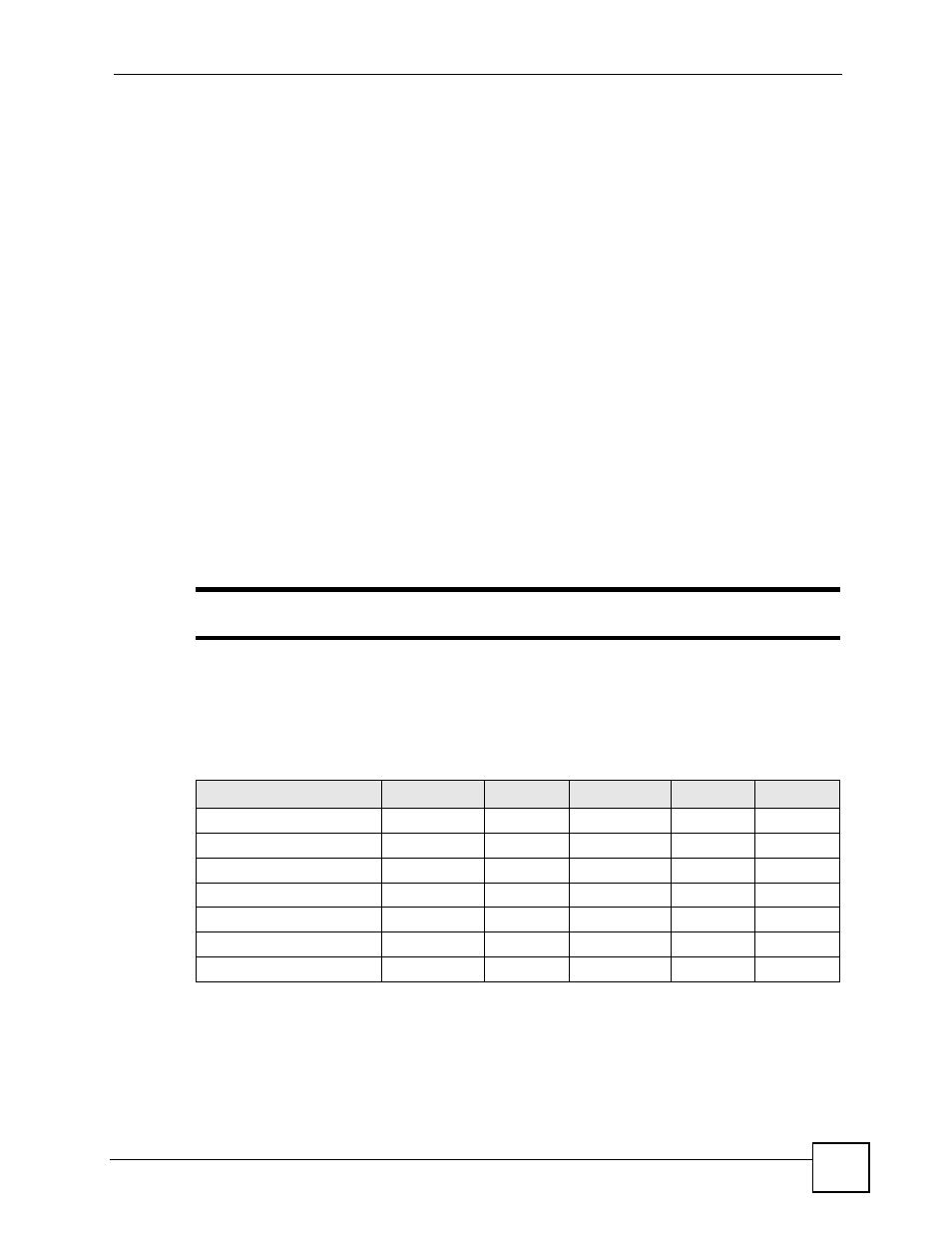
Table 29 Comparison of EAP Authentication Types
EAP-MD5
EAP-TLS
EAP-TTLS
PEAP
LEAP
Mutual Authentication
No
Yes
Yes
Yes
Yes
Certificate – Client
No
Yes
Optional
Optional
No
Certificate – Server
No
Yes
Yes
Yes
No
Dynamic Key Exchange
No
Yes
Yes
Yes
Yes
Credential Integrity
None
Strong
Strong
Strong
Moderate
Deployment Difficulty
Easy
Hard
Moderate
Moderate
Moderate
Client Identity Protection
No
No
Yes
Yes
No
