Rationale, Ecurity, Bjectives – Nortel Networks Nortel Network VPN Router and Client Workstation 7.05 User Manual
Page 52: Ationale, Able, Elationship of, Hreats to, 8 rationale, 1 security objectives rationale
Security Target, Version 3.9
March 18, 2008
Nortel VPN Router v7.05 and Client Workstation v7.11
Page 52 of 67
© 2008 Nortel Networks
8 Rationale
This section provides the rationale for the selection of the security requirements, objectives, assumptions, and
threats. In particular, it shows that the security requirements are suitable to meet the security objectives, which in
turn are shown to be suitable to cover all aspects of the TOE security environment.
8.1 Security Objectives Rationale
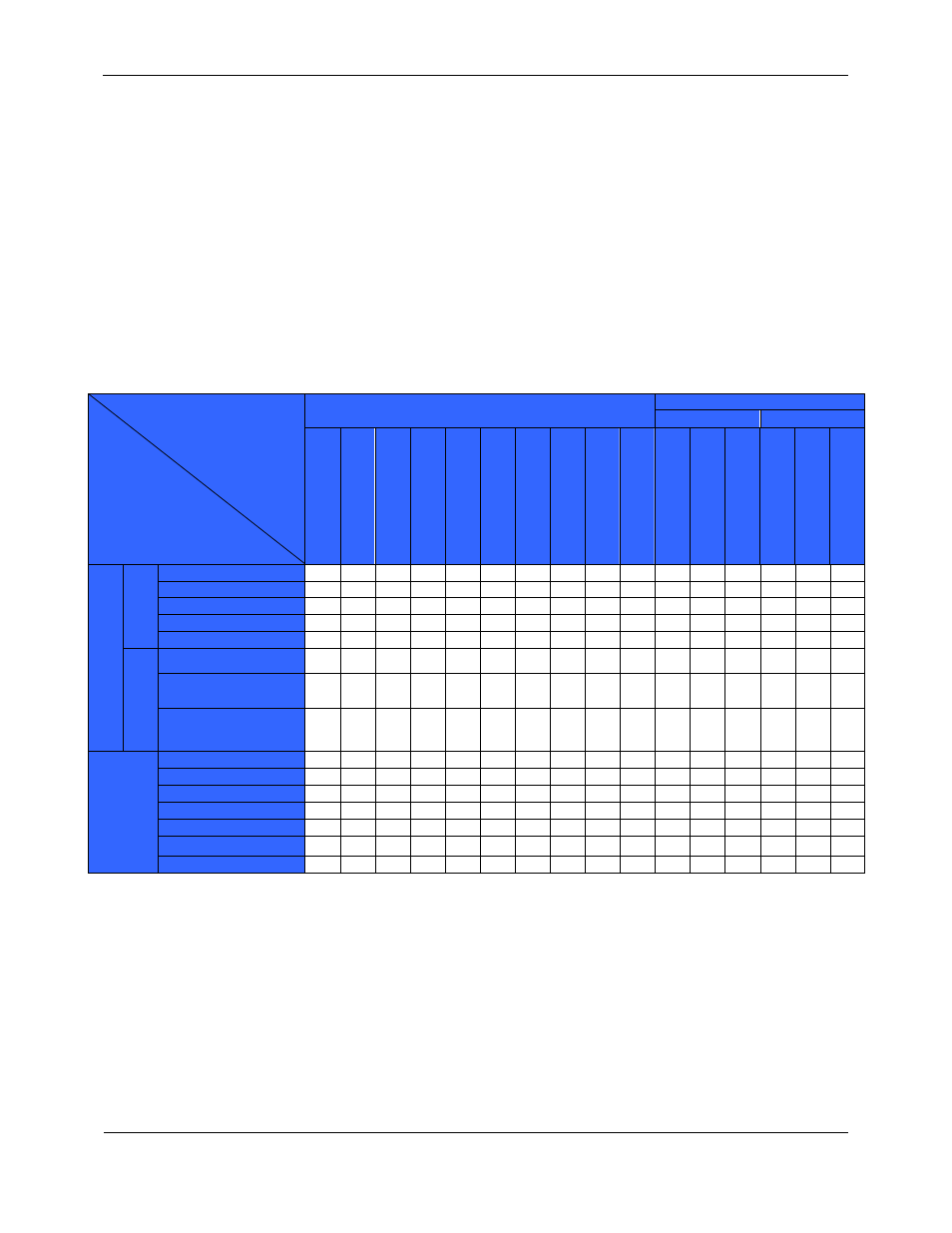
This section provides a rationale for the existence of each assumption, threat, and policy statement that compose the
Security Target. Table 11 demonstrates the mapping between the assumptions, threats, and polices to the security
objectives is complete. The following discussion provides detailed evidence of coverage for each assumption,
threat, and policy.
Table 11 - Relationship of Security Threats to Objectives
TOE Objectives
Environmental Objectives
IT
Non-IT
O
.I
&A
O
.AUDIT
O
.SEL
FPRO
TECT
O
.CO
NFIDENT
O
.I
NTEG
RITY
O
.F
IL
TER
O
.F
UN
CTION
S
O
.ADM
IN
O
.T
EST
O
.REPL
AY
O
E.T
IM
E
O
E.CERTIF
ICATE
O
E.DO
M
SEP
O
E.PHYS
-SEC
O
E.T
RAINED
O
E.DEL
IVERY
Th
rea
ts
TOE
T.UNDETECT
T.AUTH-ERROR
T.DATA-MOD
T.HACK-CRYPTO
T.HACK
TOE
Env
iron
m
e
nt
TE.PHYSICAL
TE.AUDIT_FAILURE
TE.BAD_CERT
Ass
um
pti
o
ns
A.TRAINED-ADMIN
A.TIMESTAMPS
A.PHYSICAL
A.CERTIFICATE
A.INSTALL
A.ACCESS
A.DOMSEP
T.UNDETECT An attacker may gain undetected access due to missing, weak, and/or incorrectly
implemented access controls for the restricted files or TSF Data in order to cause violations
of integrity, confidentiality, or availability of the information protected by and flowing
through the TOE.
The TOE identifies and authenticates users prior to allowing access to TOE functions and data
(O.I&A). The TOE records audit records for data accesses and use of the System functions
(O.AUDIT). The TOE provides functionality that enables only authorized user to establish VPN
sessions with the TOE using IPSec protocol (O.FUNCTIONS). The TOE provides functionality
that enables testing of its correct functioning and integrity (O.TEST).
O.I&A, O.AUDIT, O.FUNCTIONS, and O.TEST combined ensure that this threat is removed.
