2 getting real keys, Getting real keys – Sun Microsystems J2ME User Manual
Page 65
Chapter 6
Security and MIDlet Signing
53
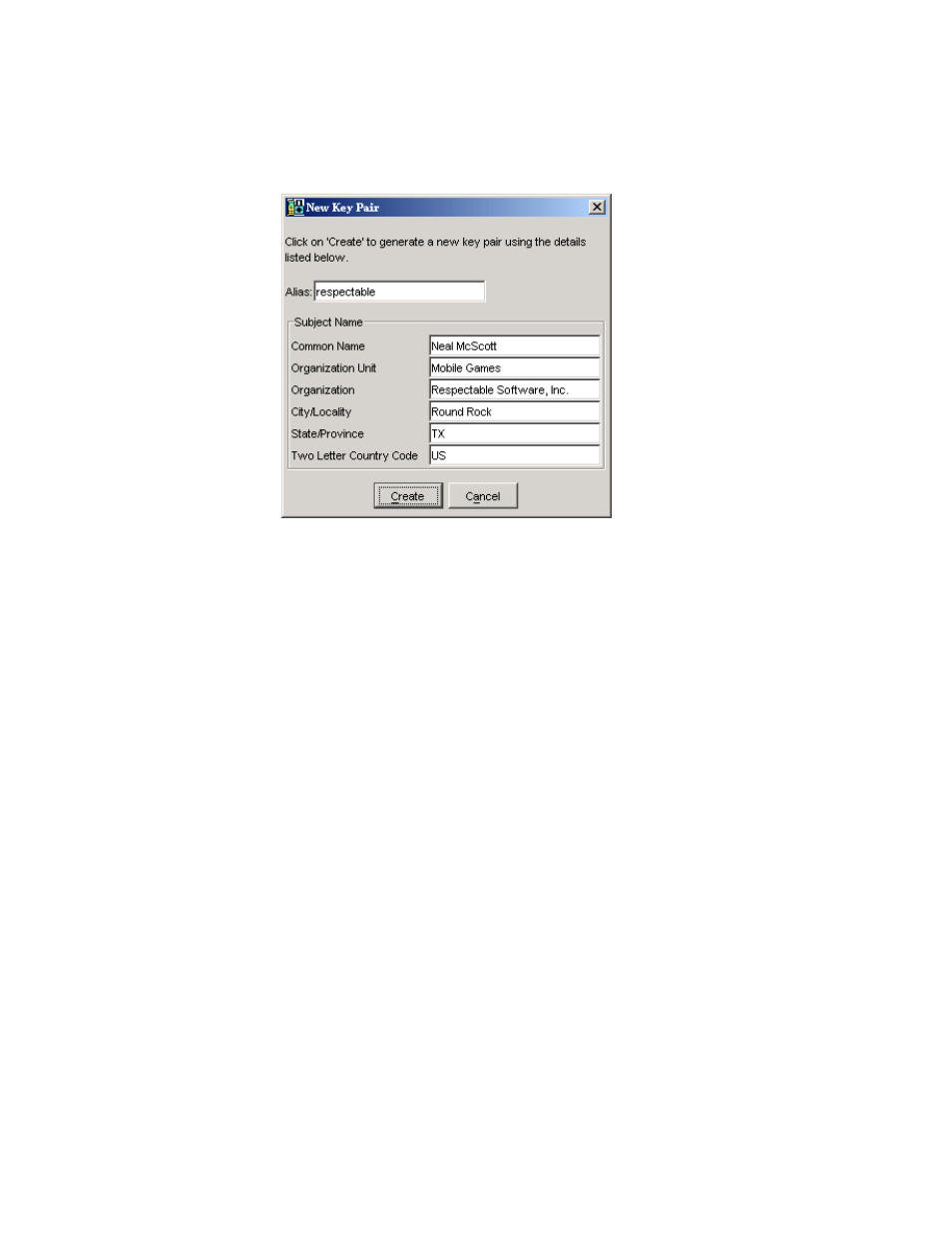
FIGURE 27
Creating a new key pair
After you click on Create, the toolkit prompts you to choose a protection domain.
The connection between the key pair you just created and a protection domain
might seem oblique, but it makes perfect sense:
■
The toolkit creates a self-signed root certficate using the key pair you just
created.
■
The root certificate is added to the emulator’s list of root certificates.
■
The toolkit needs to associate the root certificate with a protection domain.
Now imagine what happens when you install a MIDlet suite signed with your new
key:
■
The implementation examines the certificate chain in the MIDlet suite descriptor.
In this case the certificate chain is a single certificate, the self-signed root.
■
The implementation tries to find the root of the certificate chain in its internal
list. This succeeds because the root certificate was added when you create the
key pair.
■
The implementation considers the certificate valid and uses it to verify the
signature on the MIDlet suite.
■
The MIDlet suite is installed into whatever protection domain you picked.
6.4.2
Getting Real Keys
The ability to create a key pair and sign a MIDlet within the J2ME Wireless Toolkit
environment is for testing purposes only. When you run your application on an
actual device, you must obtain a signing key pair from a certificate authority
recognized by the device.
