IBM Novell 10 SP1 EAL4 User Manual
Page 196
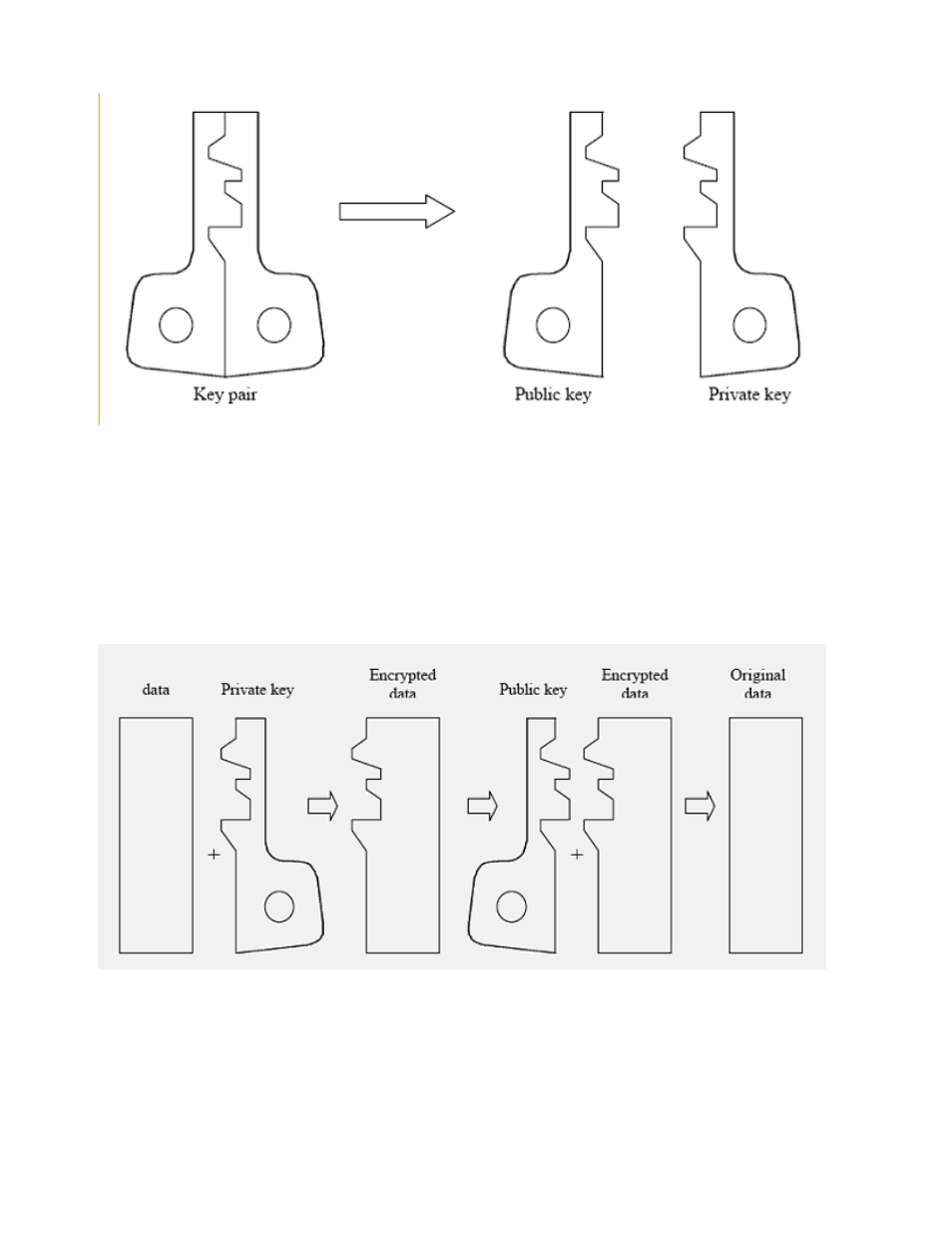
If encryption is done with a public key, only the corresponding private key can be used for decryption. This
allows a user to communicate confidentially with another user by encrypting messages with the intended
receiver’s public key. Even if messages are intercepted by a third party, the third party cannot decrypt them.
Only the intended receiver can decrypt messages with his or her private key. The following diagram
conceptually illustrates encryption with a public key to provide confidentiality.
184
Figure 5-88: Asymmetric keys
Figure 5-89: Encryption with private key provides authentication
See also other documents in the category IBM Computers:
- I5 (59 pages)
- 2274 (183 pages)
- X3650 (18 pages)
- P5 570 (82 pages)
- 6E1 (40 pages)
- 704 (348 pages)
- SG24-4576-00 (235 pages)
- SCOD-3ZVQ5W (548 pages)
- LOTUS TEAM WORKPLACE 6.5.1 (17 pages)
- HANDBOOK 150 (286 pages)
- 6C4 (233 pages)
- 6059 (248 pages)
- 6644 (100 pages)
- 2283 (96 pages)
- 755 (47 pages)
- PANEL1173-841 (80 pages)
- G325-2585-02 (90 pages)
- BladeCenter T Type 8730 (180 pages)
- PC Server/Enterprise Racks 9QX (208 pages)
- X3620 M3 (19 pages)
- NETVISTA X40 6643 (120 pages)
- 440 (202 pages)
- xSeries 235 (66 pages)
- 47AE - 410168 (27 pages)
- TotalStorage DS6000 Series (406 pages)
- 310E (120 pages)
- NETVISTA 8319 (52 pages)
- A40P TYPE 6841 (148 pages)
- POWER 710 (45 pages)
- LCD PC (50 pages)
- 525 (33 pages)
- BladeCenter 8677 (104 pages)
- N2800e (82 pages)
- 6345 (214 pages)
- 2197 (208 pages)
- 4194 (84 pages)
- V7.2 (41 pages)
- SC34-6814-04 (953 pages)
- 6268 (53 pages)
- Enterprise Server H80 Series (230 pages)
- 6.00E+01 (42 pages)
- G544-5774-01 (56 pages)
- z/OS (88 pages)
- Aptiva 2140 (212 pages)
- GC23-7753-05 (56 pages)
