Access control, Wireless security, Procedure (see – RCA SpeedTouch 580 User Manual
Page 21: Chapter 3
Chapter 3
Internet Access in No Time
E-DOC-CTC-20050126-0005 v1.0
19
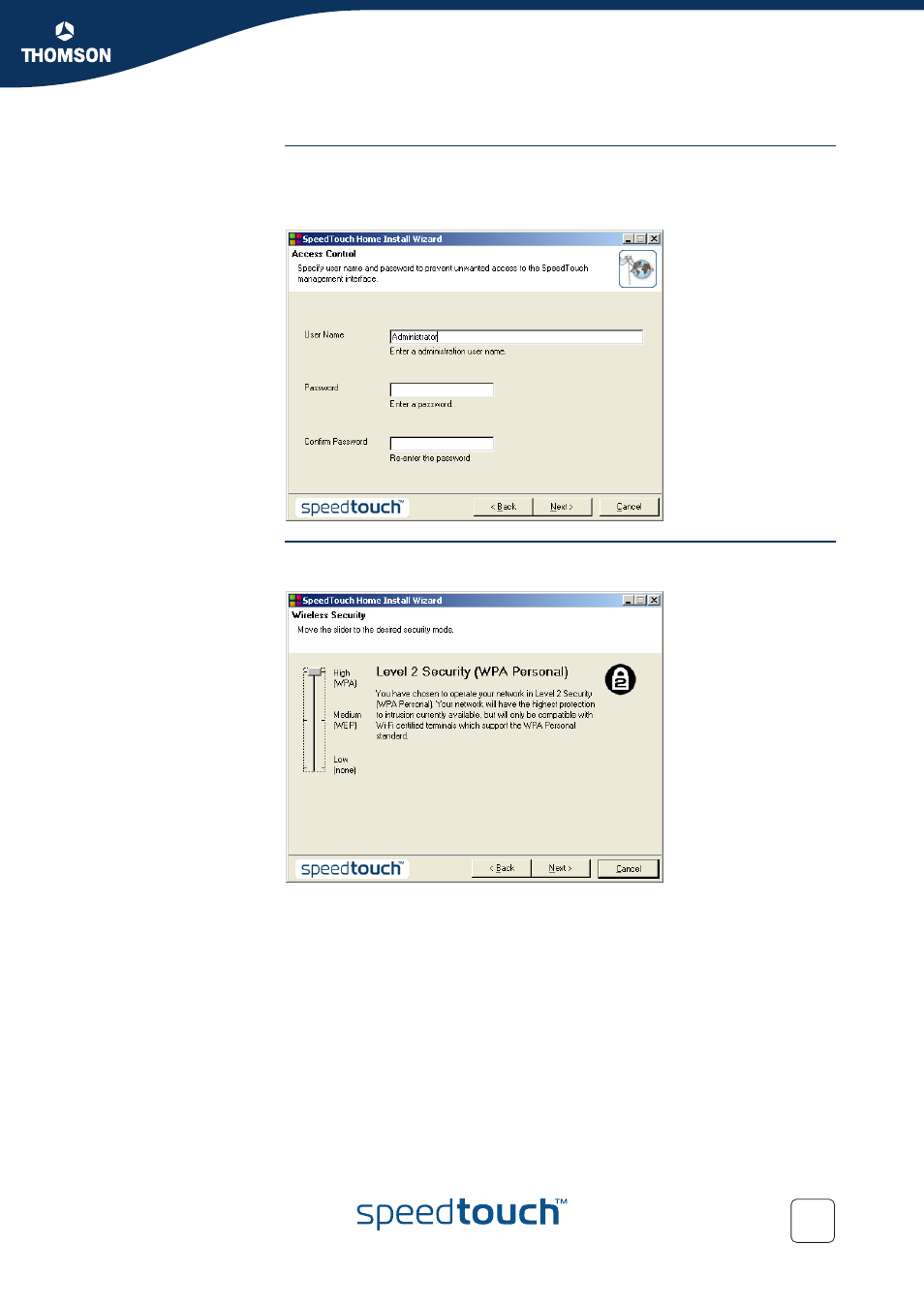
Access Control
To protect your SpeedTouch™ from unauthorized access, you must provide a user
name and password. Each time a user wants to access the SpeedTouch™ web
interface, the user will be prompted to provide this user name and password before
access is granted.
Wireless security
To protect the wireless connections to your SpeedTouch™, move the slide control to
the desired security mode.
Following security modes to secure traffic between the SpeedTouch™ and connected
wireless stations are available:
Low
, which implies in fact that no security measures are taken at all
Medium
, implying that traffic is encrypted by means of a static encryption key
(WEP).
High
, providing the highest security available (WPA) for securing all wireless
traffic.
For an overview on all SpeedTouch™ wireless security features, see
