Wr1500, Port wireless dsl/cable router – ParkerVision WR1500 User Manual
Page 84
WR1500
4-Port Wireless DSL/Cable Router
®
86
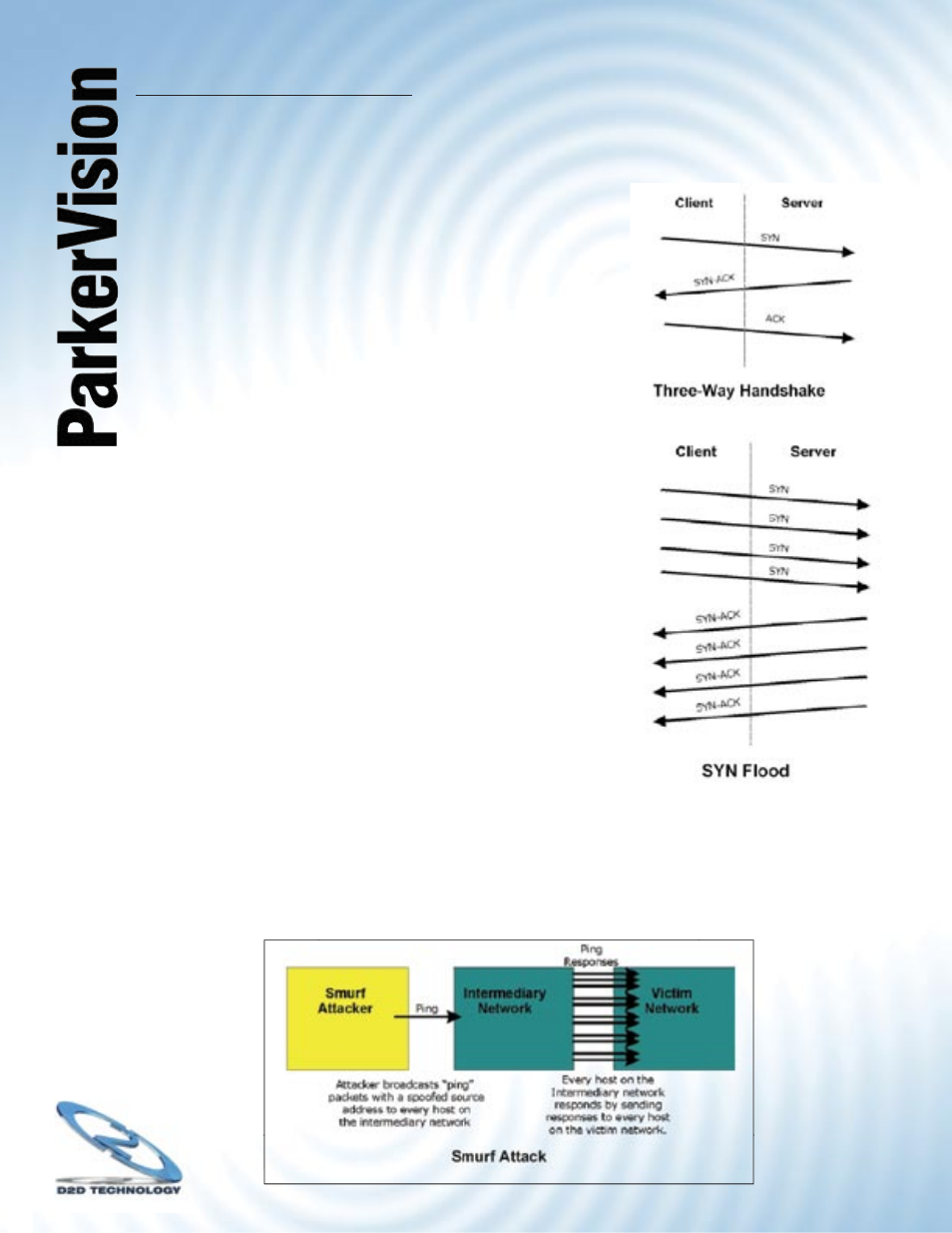
11.4.2 Types of DoS Attacks - Continued
Under normal circumstances, the application that initiates a
session sends a SYN (synchronize) packet to the receiving
server. The receiver sends back an ACK (acknowledgment)
packet and its own SYN, and then the initiator responds
with an ACK (acknowledgment). After this handshake, a
connection is established.
2. a) A
SYN Attack fl oods a targeted system with a series
of SYN packets. Each packet causes the targeted system
to issue a SYN-ACK response. While the targeted system
waits for the ACK that follows the SYN-ACK, it queues up
all outstanding SYN-ACK responses on what is known as
a backlog queue. SYN-ACKs are moved off the queue only
when an ACK comes back or when an internal timer (which
is set at relatively long intervals) terminates the three-way
handshake. Once the queue is full, the system will ignore all
incoming SYN requests, making the system unavailable for
legitimate users.
2. b) In a
LAND Attack, hackers fl ood SYN packets into the
network with a spoofed source IP address of the targeted
system. This makes it appear as if the host computer sent
the packets to itself, making the system unavailable while the
target system tries to respond to itself.
3. A
brute-force attack, such as a “Smurf’ attack, targets
a feature in the IP specifi cation known as directed or subnet
broadcasting, to quickly fl ood the target network with useless
data. A Smurf hacker fl oods a router with Internet Control
Message Protocol (ICMP) echo request packets (pings).
Since the destination IP address of each packet is the
broadcast address of the network, the router will broadcast
the ICMP echo request packet to all hosts on the network.
If there are numerous hosts, this will create a large
amount of ICMP echo request and response traffi c. If a hacker chooses to spoof the source IP
address of the ICMP echo request packet, the resulting ICMP traffi c will not only clog up the
“intermediary” network, but will also congest the network of the spoofed source IP address,
known as the “victim” network.
This fl ood of broadcast traffi c consumes all available bandwidth, making communications
impossible.
