2 access control list, 4 misc configuration – Planet Technology FGSW-2620VM User Manual
Page 64
FGSW-2620VM User’s Manual
4.5.1.4 Misc Configuration
The section provides 802.1x-Misc Configuration, the screen in
Figure 4-5-3
Figure 4-5-3
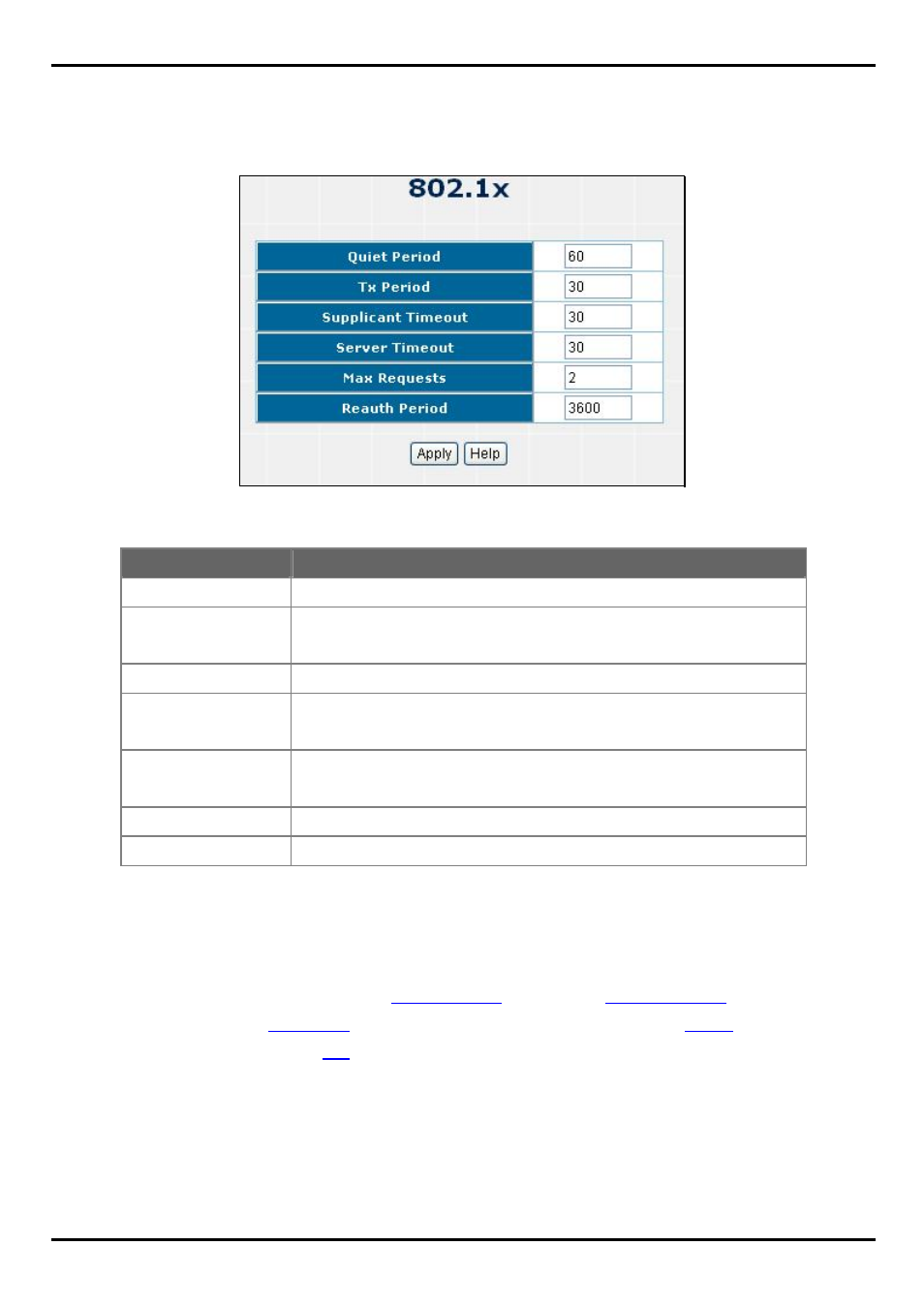
802.1x Configuration - Misc Configuration interface
OObject
Description
Set the period during which the port doesn't try to acquire a supplicant.
Quiet Period
Set the period the port waits to retransmit next EAPOL PDU during an
authentication session.
Tx Period
Set the period of time the switch waits for a supplicant response to an EAP request.
Supplicant Timeout
Set the period of time the switch waits for a server response to an authentication
request.
Server Timeout
Set the number of authentication that must time-out before authentication fails and
the authentication session ends.
Max Requests
Set the period of time after which clients connected must be re-authenticated.
Reauth Period
Apply Button
Press this button to save the 802.1x’s value on the Switch.
4.5.2 Access Control List
The Access Control List (ACL) is a concep
d
. It is a means of
determining the appropriate
n object depending on certain aspects of the
that is making
the request, principally the process'
identifier. Access Control List (ACL) is a mechanism that implements
access control for a system resource by listing the identities of the system entities that are permitted or denied to access
the resource. The screen in following screen appears.
64
