Chapter 1: introduction, Introduction to vpns, Vpn examples – Linksys BEFVP41 User Manual
Page 5: Introduction to vpns vpn examples, Introduction, Vpn router to vpn router, Computer (using vpn client software) to vpn router
Chapter 1
Introduction
1
EtherFast Cable/DSL VPN Router with 4-Port Switch
Chapter 1:
Introduction
Thank you for choosing the Linksys by Cisco EtherFast
Cable/DSL VPN Router with 4-Port Switch. The Router
lets you access the Internet through its four switched
ports. You can also use the Router to share resources
such as computers, printers and files. A variety of security
features help to protect your data and your privacy while
online. Security features include Virtual Private Network
(VPN) technology and a Stateful Packet Inspection (SPI)
firewall. Configuring the Router is easy using the provided
browser-based utility.
Introduction to VPNs
A VPN is a connection between two endpoints—a VPN
Router, for instance—in different networks that allows
private data to be sent securely over a shared or public
network, such as the Internet. This establishes a private
network that can send data securely between these two
locations or networks.
The private network is established by creating a “tunnel”.
A VPN tunnel connects the two computers or networks
and allows data to be transmitted over the Internet
as if it were still within those networks. A VPN tunnel
uses industry-standard encryption and authentication
techniques to secure the data sent between the two
networks.
Virtual Private Networking was created as a cost-effective
alternative to using a private, dedicated, leased line for a
private network. It can be used to create secure networks
linking a central office with branch offices, telecommuters,
and/or professionals on the road.
There are two basic ways to create a VPN connection:
VPN Router to VPN Router
•
computer (using VPN client software) to VPN Router
•
The VPN Router creates a “tunnel” or channel between two
endpoints, so that data transmissions between them are
secure. A computer with VPN client software can be one
of the two endpoints.
For an Internet Protocol Security (IPSec) VPN tunnel, the
VPN Router and any computer with the built-in IPSec
Security Manager (Windows 2000 and XP) can create a VPN
tunnel using IPSec (Windows Vista uses a similar utility).
Other Windows operating systems require additional,
third-party VPN client software applications that support
IPSec to be installed.
VPN Examples
The following are examples of a VPN tunnel between two
VPN routers and a VPN tunnel between a computer using
VPN client software and a VPN router.
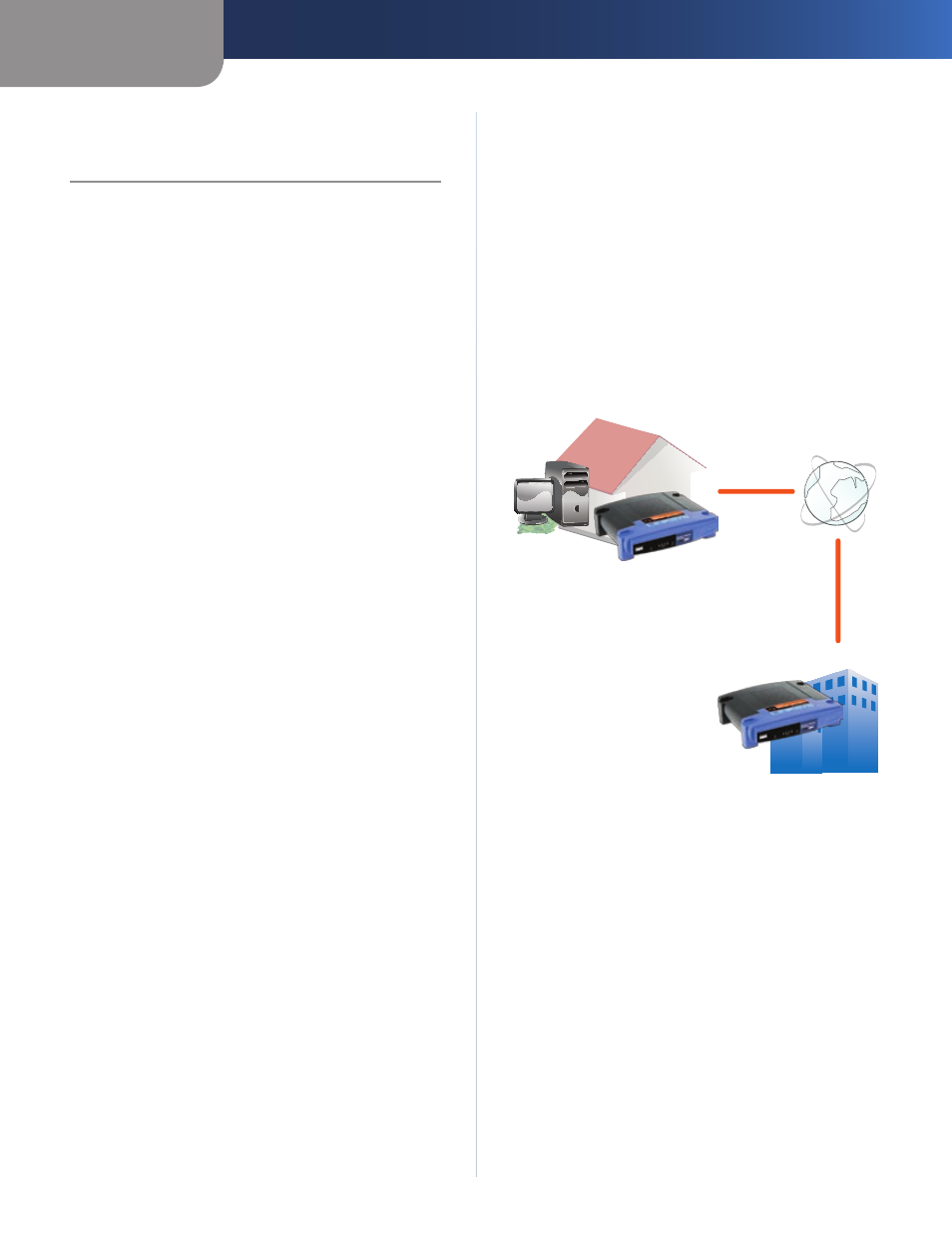
VPN Router to VPN Router
For example, at home, a telecommuter uses his VPN
Router for his always-on Internet connection. His Router
is configured with his office’s VPN settings. When he
connects to his office’s router, the two routers create a
VPN tunnel, encrypting and decrypting data. As VPNs use
the Internet, distance is not a factor. Using the VPN, the
telecommuter now has a secure connection to the central
office’s network, as if he were physically connected.
Internet
Central Office
Home
VPN Router
VPN Router
VPN Router to VPN Router
Computer (using VPN client software) to
VPN Router
The following is an example of a computer-to-VPN Router
VPN. In her hotel room, a traveling businesswoman
connects to her Internet Service Provider (ISP). Her
notebook computer has VPN client software that is
configured with her office’s VPN settings. She accesses
the VPN client software and connects to the VPN Router
at the central office. As VPNs use the Internet, distance is
not a factor. Using the VPN, the businesswoman now has a
secure connection to the central office’s network, as if she
were physically connected.
