Equinox Systems ZyAIR G-200 User Manual
Page 33
ZyAIR G-200 User’s Guide
Using the ZyAIR Utility
2-15
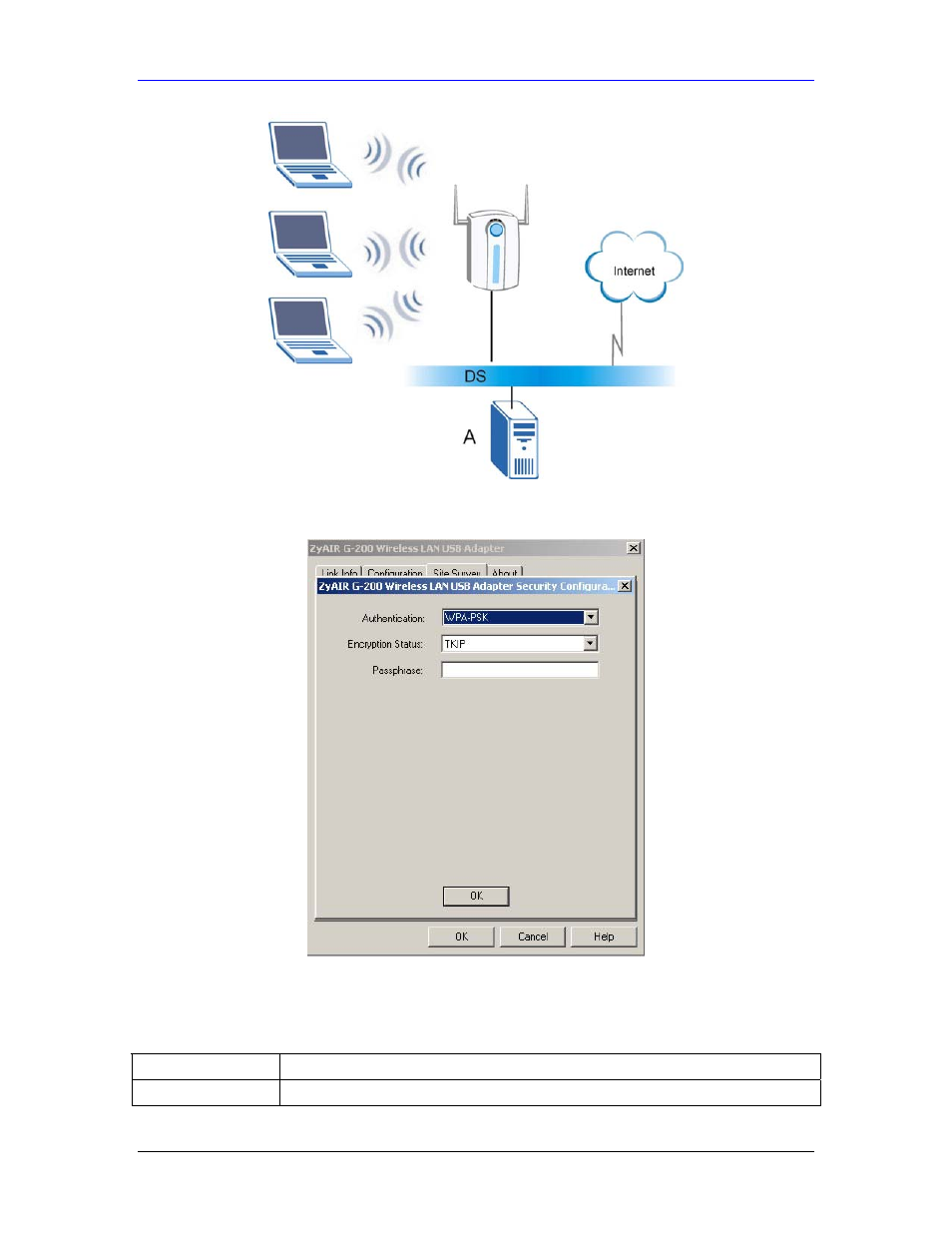
Figure 2-13 WPA with RADIUS Application Example
Figure 2-14 WPA-PSK Authentication
Follow the instructions in the table to configure the WEP encryptions.
Table 2-6 WPA-PSK Authentication
FIELD DESCRIPTION
Authentication
Select WPA-PSK from the drop-down list box.
