Konig Electronic WLAN router 300 Mbps User Manual
Page 29
29
Packet Filter enables you to control what packets are allowed to pass the router. Outbound filter applies
on all outbound packets. However, inbound filter applies on packets that are destined to virtual servers
or DMZ host only. You can select one of the two filtering policies:
1. Allow all to pass except those that match the specified rules
2. Deny all to pass except those that match the specified rules
You can specify 8 rules for each direction: inbound or outbound. For each rule, you can define the
following:
• Source IP address
• Source port address
• Destination IP address
• Destination port address
• Protocol: TCP or UDP or both.
• Use Rule#
For source or destination IP address, you can define a single IP address (4.3.2.1) or a range of IP
addresses (4.3.2.1-4.3.2.254). If no prefix has been added, all port addresses will apply.
For source or destination port, you can define a single port (80) or a range of ports (1000-1999). Add
prefix "T" or "U" to specify TCP or UDP protocol. For example, T80, U53, U2000-2999. No prefix
indicates both TCP and UDP are defined. An empty implies all port addresses. Packet Filter can work
with Schedule Rules, and give user more flexibility on access control. For details, please refer to
Schedule Rule.
Each rule can be enabled or disabled individually.
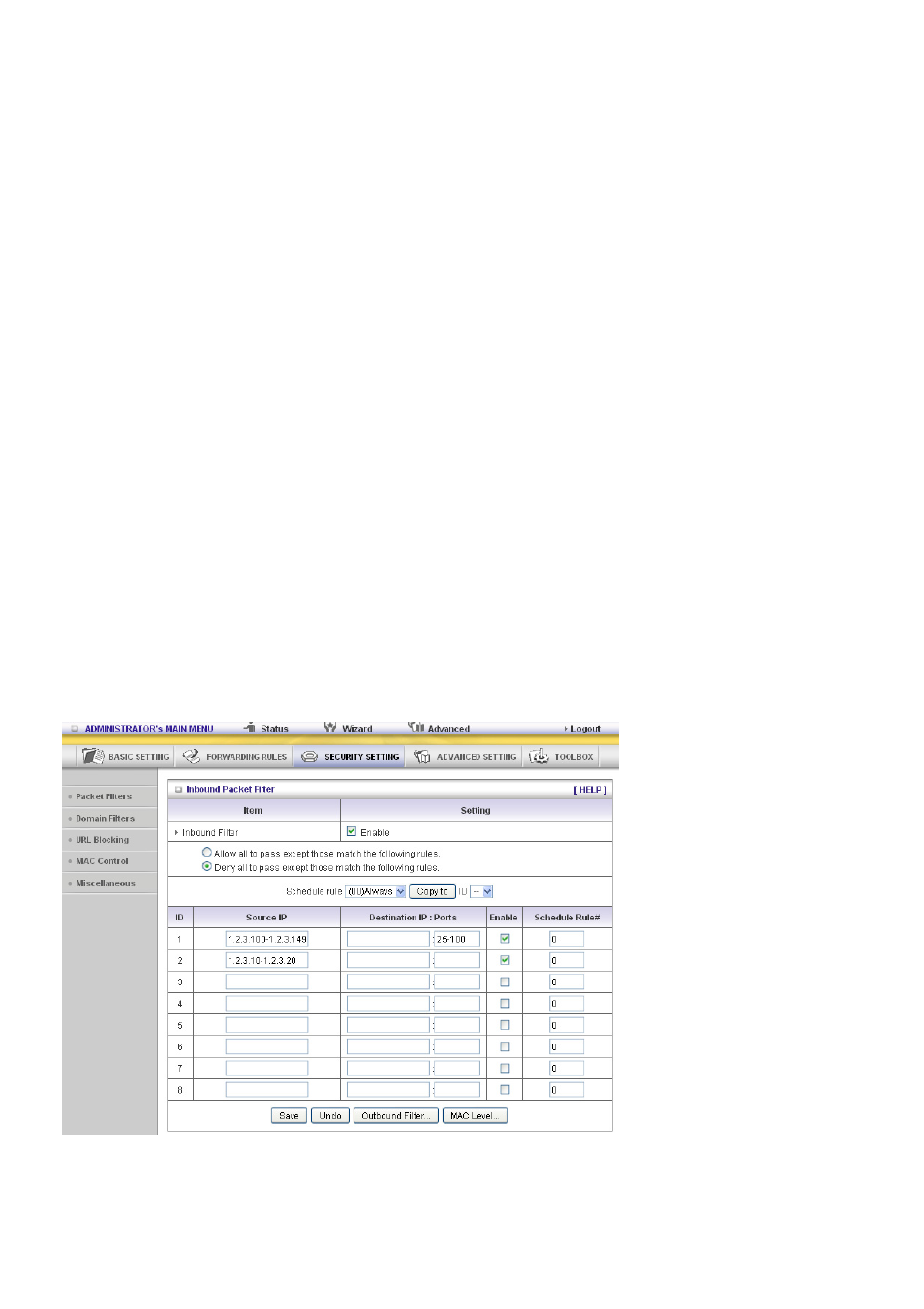
Inbound Filter:
To enable Inbound Packet Filter click the check box next to Enable in the Inbound Packet Filter
field.
Suppose you have SMTP Server (25), POP Server (110), Web Server (80), FTP Server (21), and News
Server (119) defined in Virtual Server or DMZ Host.
Example 1:
(1.2.3.100-1.2.3.149) Remote hosts are allowed to send mail (port 25), and browse the Internet
(port 80)
(1.2.3.10-1.2.3.20) Remote hosts can do everything (block nothing)
Others are all blocked.
