WatchGuard VPN v10.0 User Manual
Page 16
Modifying an Existing Mobile VPN Profile
14
Mobile User VPN
timeouts for the Mobile VPN group are always ignored because you set timeouts in the
individual Firebox user accounts.
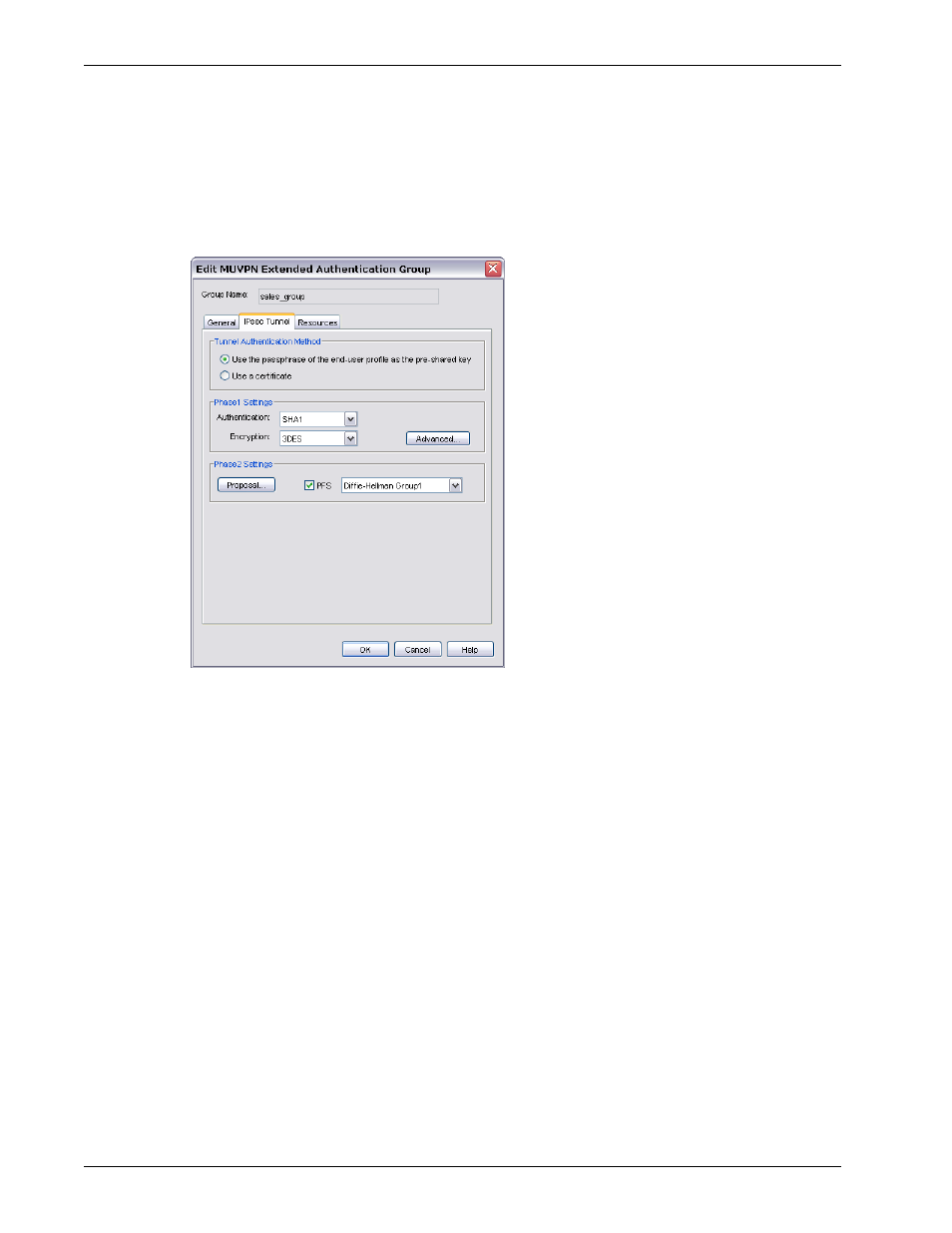
The session and idle timeouts cannot be longer than the value in the SA Life field. To set this
field, from the IPSec Tunnel tab of the Edit MUVPN Extended Authentication Group dialog
box, click Advanced. The default value is 8 hours.
4
Click the IPSec Tunnel tab.
5
Use the following fields to edit the IPSec settings:
Use the passphrase of the end-user profile as the pre-shared key
Select this setting to use the passphrase of the end-user profile as the pre-shared key for tunnel
authentication. You must use the same shared key on the remote device, and this shared key can
use only standard ASCII characters.
Use a certificate
Select this setting to use a certificate for tunnel authentication. You must start the WatchGuard
Certificate Authority if you select certificate-based authentication. You must also use the
WatchGuard Log Server for log messages and the Firebox must be a managed client of a
WatchGuard Management Server.The WatchGuard Certificate Authority is installed by default as
part of the Management Server installation.
CA IP address
(This field appears only if you select to use a certificate) Type the IP address for the certificate
authority (CA).
Timeout
(This field appears only if you select to use a certificate) Type the time in seconds before the
certificate authority request times out.
Phase1 Settings
Select the authentication and encryption methods for the Mobile VPN tunnel. These settings
must be the same for both VPN endpoints. To configure advanced settings, such as NAT Traversal
or the key group, click the Advanced button, and see the procedure described in “Defining
advanced Phase 1 settings” on page 16.
