Nortel Networks 4500 FIPS User Manual
Page 10
© Copyright 2000 Nortel Networks.
10
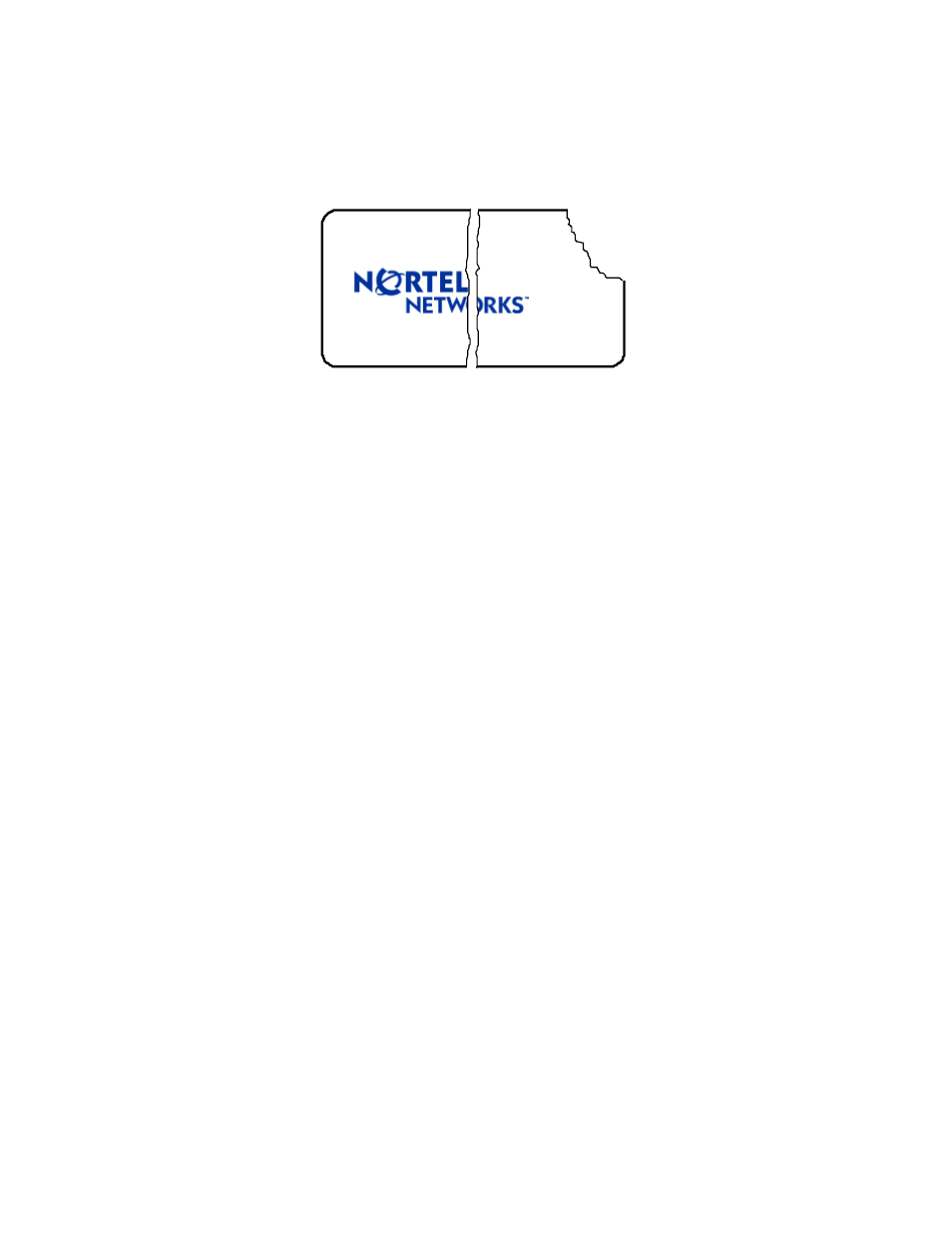
Attempting to remove a label breaks it or continually tears off small fragments as depicted in
Figure 9. Other signs of tamper-evidence include a strong smell of organic solvents, warped or
bent cover metal, and scratches in the paint on the module.
FIPS 140-1 Level 2 Tamper Evident Label
Serial Number:
5673422
Contivity
Extranet
Switch
Figure 9 – Damaged Tamper-Evident Label
2.4 Roles and Services
The Switch supports up to 5000 simultaneous users sending packets using Internet Protocol
Security (IPSec), Point-to-Point Tunneling Protocol (PPTP), Layer Two Tunneling Protocol
(L2TP), and Layer Two Forwarding (L2F). In addition, an administrator may securely
configure the switch either locally, or remotely.
The Switch employs role-based authentication of users, and stores user identity information in
an internal or an External Lightweight Directory Access Protocol (LDAP) database.
Authentication can optionally be performed against a variety of external servers using LDAP or
RADIUS (Novell NDS, Microsoft Windows NT Domains, Security Dynamics ACE Server,
Axent OmniGuard Defender)
There are two main roles in the Switch (as required by FIPS 140-1) that users may assume:
Crypto Officer role and User role. The administrator of the switch assumes the Crypto Officer
role in order to configure and maintain the switch using Crypto Officer services, while the Users
exercise only the User services. The Crypto Officer role is assumed with the following rights:
•
Manage Switch rights: (either none, view switch, or manage switch). View
switch rights allow an administrator to view all the configuration and status
information on the switch. Manage switch rights allow an administrator to
configure the switch and actually change settings.
•
Manage Users rights: (either none, view users, or manage users). View users
rights allow an administrator to review all user accounts and settings on the Switch
while manage users rights actually allow an administrator to create, modify, and
delete users.
A User authenticates and assumes the User role in order to have rights to access the following
services:
