Drop-in configuration (figure 2), Using a secondary network (figure 3) – WatchGuard Firebox X Core User Manual
Page 3
3
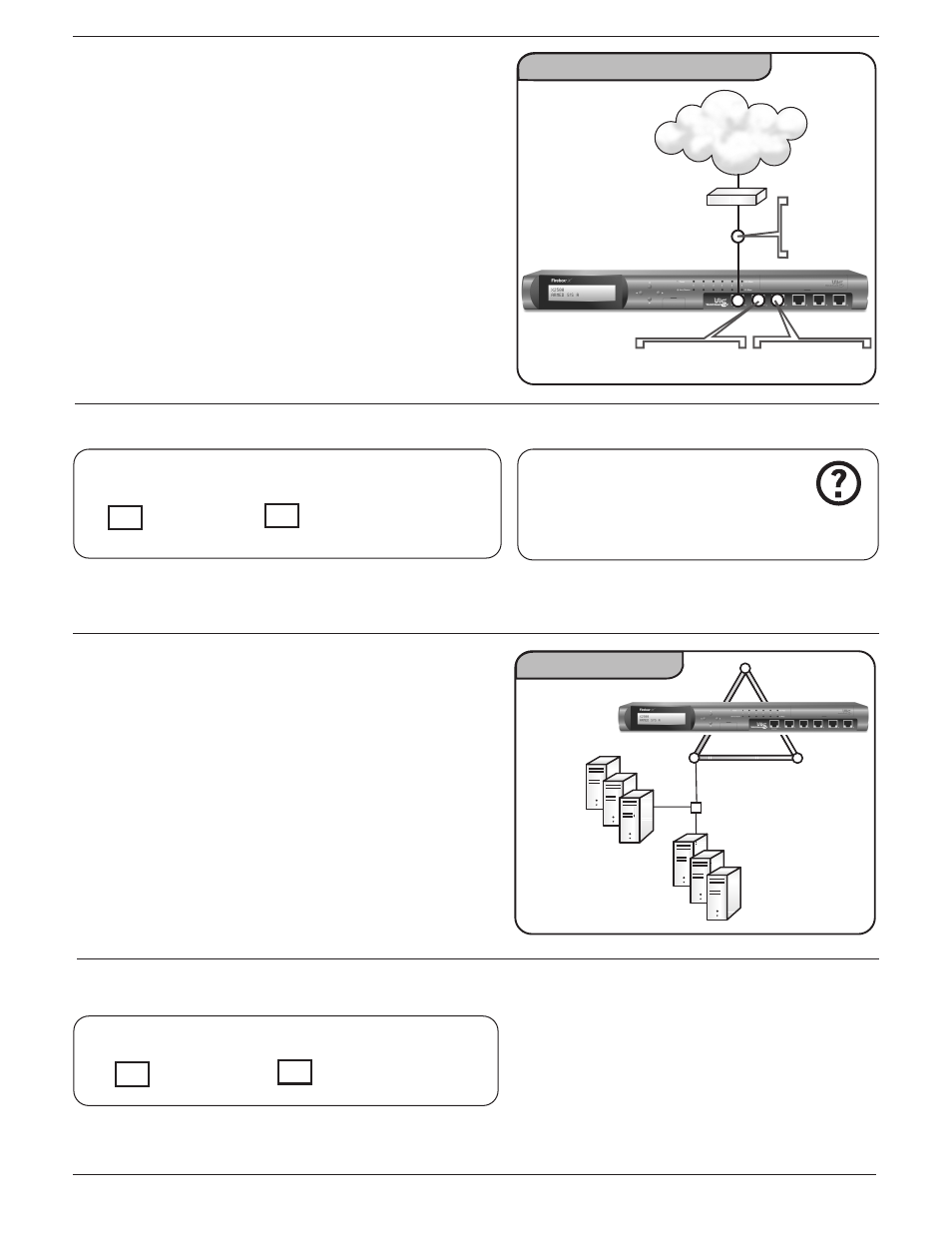
Drop-in Configuration (Figure 2)
This configuration is necessary when Public servers
behind the Firebox use public addresses, and traffic is
routed through the Firebox with no network address
translation. The Firebox is put in place with the same
network address on all interfaces. Because this config-
uration mode distributes the network’s logical address
space across the Firebox interfaces, you can “drop”
the Firebox between the router and the LAN without
reconfiguring any local machines.
Using a Secondary Network
(Figure 3)
Whether you have chosen Routed or Drop-in mode,
your configuration may require a secondary network
on the trusted interface. A secondary network is a
separate logical network connected to the Firebox
interface by a switch or hub.
Note: The IP address you declare as a secondary net-
work becomes the default gateway for computers on
that network.
Figure 2
Option 2: Drop-in Configuration
Optional Interface
66.4.5.2/24
Trusted Interface
66.4.5.2/24
Router
66.4.5.1/24
External
Interface
66.4.5.2/24
Internet
Figure 3
10.10.10.254 (Primary)
172.16.1.10
172.16.1.15
172.16.1.20
Trusted Interface
Hub/
Switch
10.10.10.1
10.10.10.5
10.10.10.25
Primary
Network
Secondary Network
172.16.1.254 (Secondary)
Secondary Network
QUESTIONS
For more information about Routed or
Drop-in Configurations, please refer to the
Getting Started section of the User Guide.
FIREWALL CONFIGURATION MODE
Routed
Drop-in
SECONDARY NETWORK
YES
NO
