3 network security, 1 network ports, 2 ip filtering – Konica Minolta IC-308 User Manual
Page 5: 3 network encryption
5
3 Network Security
Standard network security features on the Fiery server include
the ability to permit only authorized users and groups to access
and print to the output device, limiting device communications
to designated IP addresses, and controlling the availability of
individual network protocols and ports as desired.
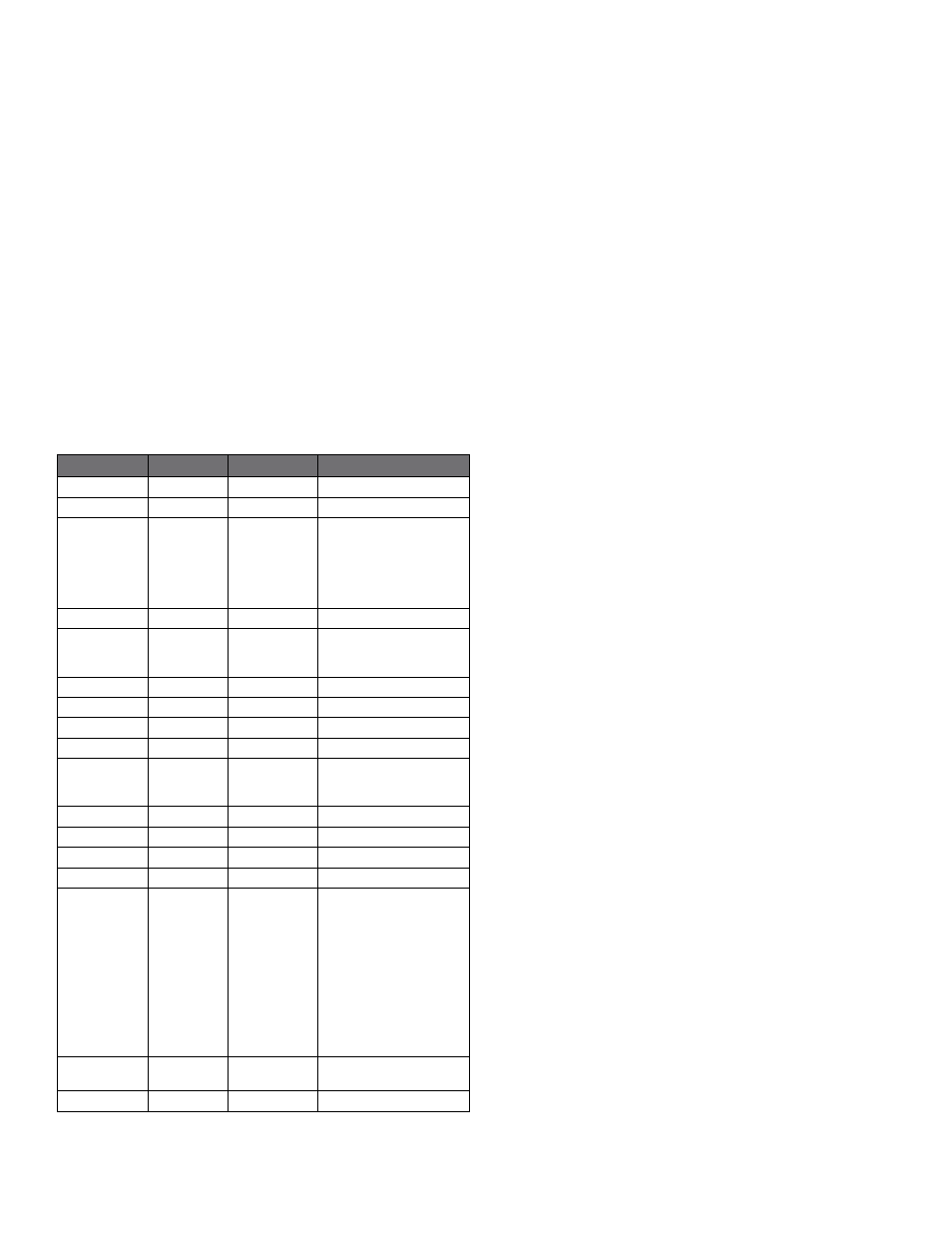
3.1 Network Ports
The Fiery server allows the network administrator the ability
to selectively enable and disable the following IP ports. As a
result, unwanted device communication and system access
via specific transport protocols can be effectively blocked.
TCP
UDP
Port Name
Dependent Service(s)
20-21
FTP
80
HTTP
WebTools, IPP
135
MS RPC
Microsoft
®
RPC Service
(Windows 7 Professional
only). An additional port in
the range 49152-65536 will
be opened to provide SMB
related point and print service.
137-139
NETBIOS
Windows Printing
161, 162
SNMP
WebTools, Fiery Central,
some legacy utilities, other
SNMP-based tools
427
SLP
443
HTTPS
WebTools, IPP/s
445
SMB/IP
SMB over TCP/IP
500
ISAKMP
IPsec
515
LPD
LPR printing, some legacy
utilities (such as WebTools,
older versions of CWS)
631
IPP
IPP
3050
Firebird
4500
IPsec NAT
IPsec
5353
Multicase DNS
Bonjour
6310
8010
8021-8022
8090
9906
18021
18022
18081
18082
21030
22000
9906
EFI ports
Command WorkStation 4
and 5, Fiery Central, EFI
SDK-based tools, Fiery
Printer Driver bi-di functions,
WebTools, and Fiery Direct
Mobile Printing, and Native
Document Conversion.
3389
RDP
Remote Desktop (Windows
Fiery servers only)
9100-9103
Printing Port
Port 9100
Other TCP ports, except those specified by the engine
manufacturers, are disabled. Any service dependent on a
disabled port cannot be accessed remotely.
The Fiery Administrator also can enable and disable the
different network services provided by the Fiery server.
The local administrator can define SNMP read and write
community names and other security settings.
3.2 IP Filtering
The Administrator can restrict authorized connections with
the Fiery server from those hosts whose IP addresses fall
within a particular IP range. Commands or jobs sent from
non-authorized IP addresses are ignored by the Fiery server.
3.3 Network Encryption
3.3.1 IPsec
IPsec or Internet Protocol security provides security to
all applications over IP protocols through encryption and
authentication of each and every packet.
The Fiery server uses pre-shared key authentication to
establish secure connections with other systems over IPsec.
Once secure communication is established over IPsec
between a client computer and a Fiery server, all
communications — including print jobs — are securely
transmitted over the network.
3.3.2 SSL and TLS
SSL/TLS are application level protocol used for transmitting
messages over the Internet securely. The Fiery server
secures http, email and LDAP communication with
SSL v2/v3 and TLS.
The Fiery server uses Lightweight Directory Access Protocol
(LDAP) to get user and group information from the Active
Directory. Simple LDAP authentication is in clear text, so it is
unsecured. The Adminstrator can secure the LDAP traffic by
enabling SSL/TLS option on Fiery server.
The Fiery server provides the Adminstrator options to
enable SSL/TLS to establish secure communication with
an email server.
The Fiery server requires a certificate for LDAP
communication over SSL or TLS. The Fiery server only
supports importing certificates and does not support
certificate generation for SSL.
