Configuring a wireless router, Protecting your wlan, Configuring a wireless router protecting your wlan – HP x360 350 G1 Convertible PC User Manual
Page 26
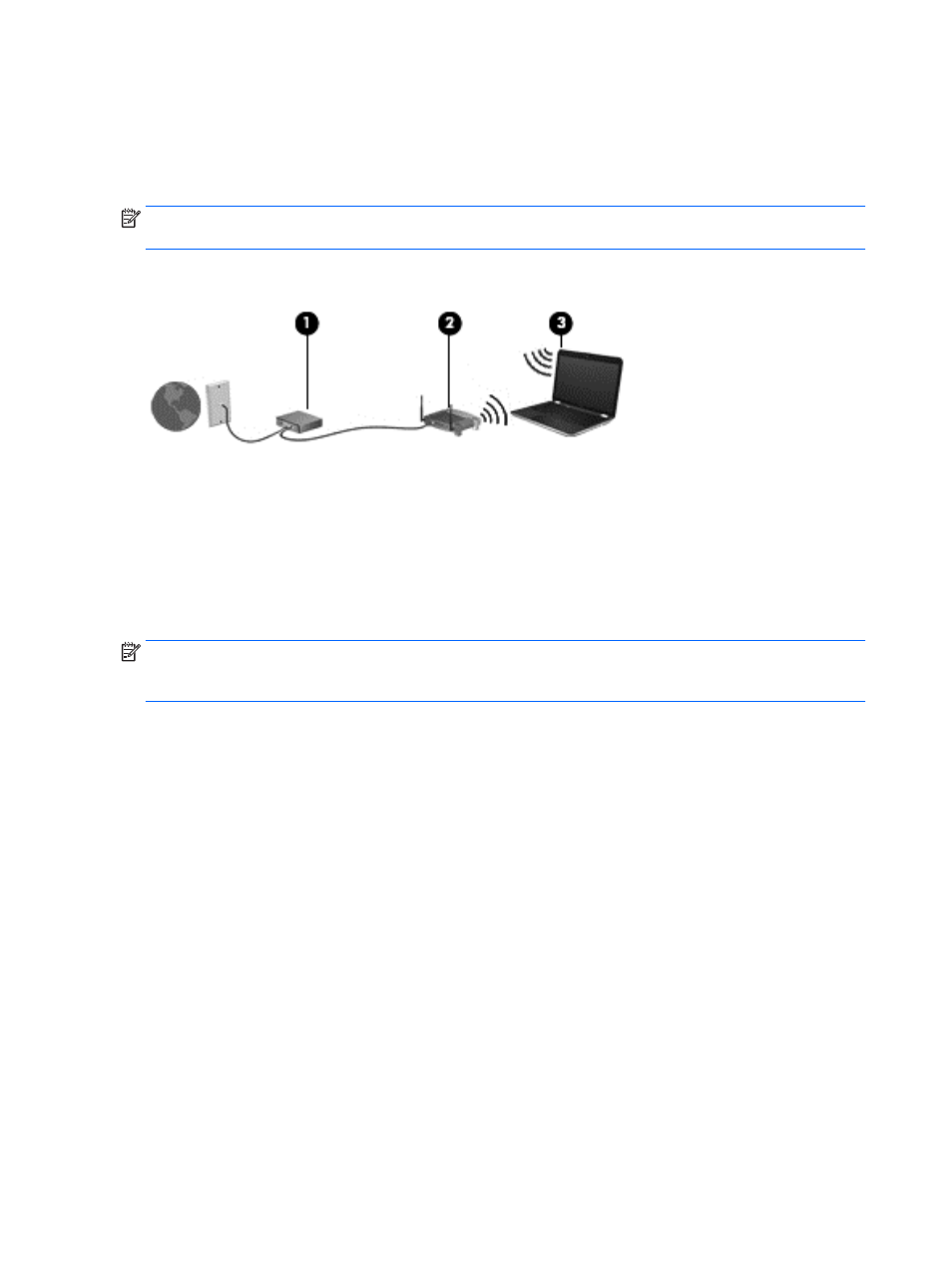
●
A broadband modem (either DSL or cable) (1) and high-speed Internet service purchased from
an Internet service provider
●
A wireless router (2) (purchased separately)
●
A wireless computer (3)
NOTE:
Some modems have a built-in wireless router. Check with your ISP to determine what type
of modem you have.
The illustration below shows an example of a wireless network installation that is connected to the
Internet.
As your network grows, additional wireless and wired computers can be connected to the network to
access the Internet.
For help in setting up your WLAN, see the information provided by your router manufacturer or your
ISP.
Configuring a wireless router
For help in configuring a wireless router, see the information provided by your router manufacturer or
your ISP.
NOTE:
It is recommended that you initially connect your new wireless computer to the router by
using the network cable provided with the router. When the computer successfully connects to the
Internet, disconnect the cable, and access the Internet through your wireless network.
Protecting your WLAN
When you set up a WLAN or access an existing WLAN, always enable security features to protect
your network from unauthorized access. WLANs in public areas (hotspots) like coffee shops and
airports may not provide any security. If you are concerned about the security of your computer when
connected to a hotspot, limit your network activities to email that is not confidential and basic Internet
surfing.
Wireless radio signals travel outside the network, so other WLAN devices can pick up unprotected
signals. Take the following precautions to protect your WLAN:
●
Use a firewall.
A firewall checks information and requests that are sent to your network, and discards any
suspicious items. Firewalls are available in both software and hardware. Some networks use a
combination of both types.
●
Use wireless encryption.
Wireless encryption uses security settings to encrypt and decrypt data that is transmitted over
the network. For more information, from the Start screen, type help, and then select Help and
Support.
18 Chapter 3 Connecting to a network
