The 700 series encryption system, Level 1, Level 2 – Lectrosonics UT700 User Manual
Page 9: Level 3
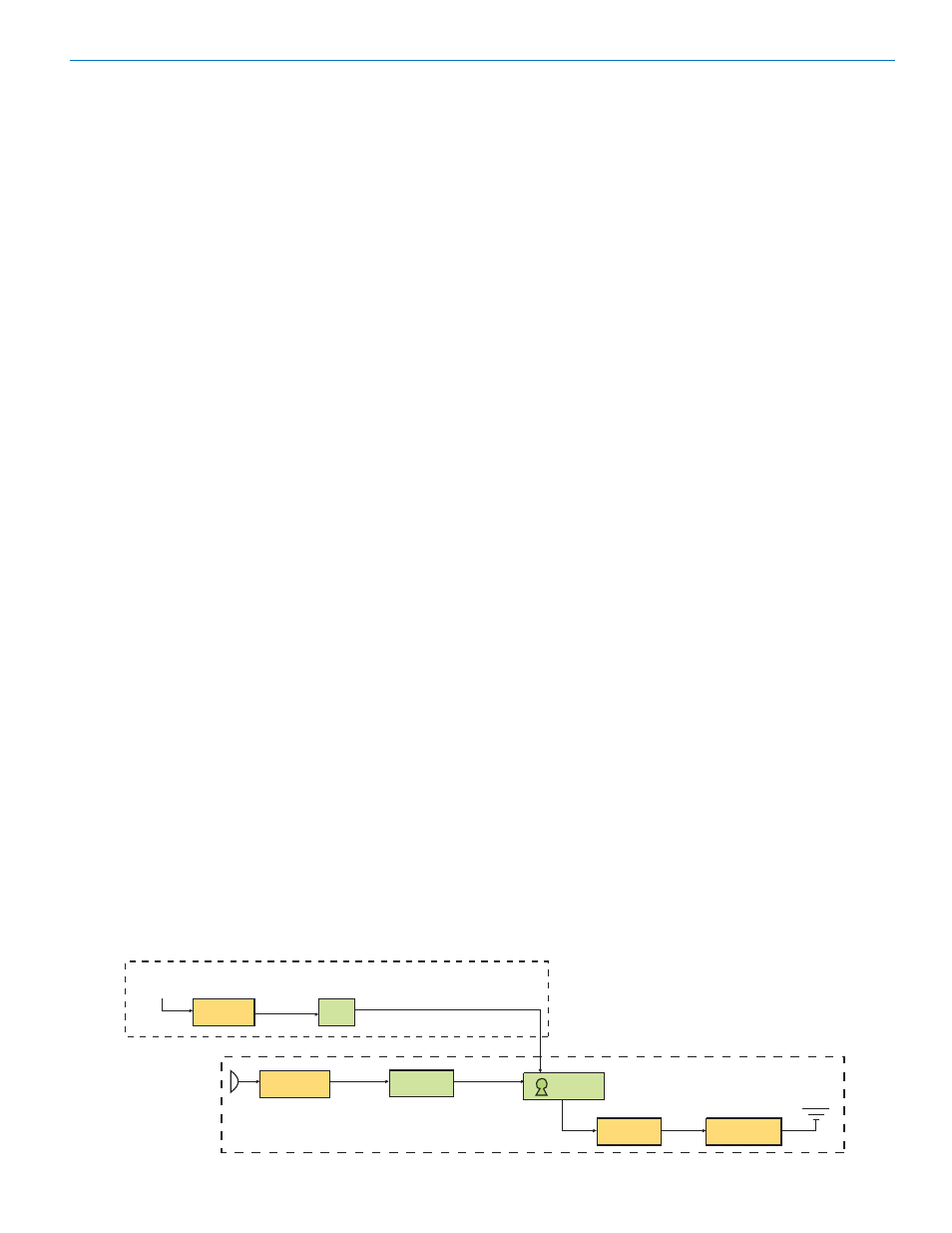
Encrypted Digital Wireless System
The 700 Series Encryption System
To guard against eavesdropping, the encryption in the 700
Series digital wireless system makes use of several
processes and a unique key setup procedure to provide a
high level of entropy and thus maximum security. A 128
bit key is used to create a formidable barrier against brute
force attacks attempting to break the encryption code.
The result is 340 trillion, trillion, trillion possible key
combinations.
The audio signal entering the transmitter first passes
through a DSP controlled, dual-envelope limiter that cleanly
limit signal peaks up to 30 dB above full modulation. The
signal is then converted to 24-bit digital audio, with sampling
at 44.1 kHz. The resulting bit stream is then digitally
compressed to meet the bandwidth requirements for the
radio output, encrypted and then transmitted over the air.
The encryption key setup procedure involves a cable
connection between the transmitter and receiver. Once
connected, the receiver maybe placed into the key
generation mode and the operator is prompted to make
several button pushes on the front panel of the receiver.
These button pushes capture the instanteneous value of a
fast, free running, 16-bit timer. The captured values are
combined to create the eight, 16-bit segments of the 128
bit encryption key.
With the exception of Security Level 3, any number of
transmitters can be connected during a single setup
procedure to share a common encryption key. Regardless
of which Security Level is selected, only one receiver can
share the key with the transmitter(s). This prevents the
use of a second receiver to eavesdrop on the transmitted
signal.
The 700 System offers three levels of security, trading off
ease of use for immunity to attack.
Level 1
Security Level 1 offers the most intuitive operation. Once
the key has been set, the equipment may be operated
exactly the same as a traditional analog system. The
transmitter and receiver may be powered on in any
sequence, and the transmitter may move in and out of
range without consequence (except normal squelching).
Security in this mode is excellent, but the scrambling
sequence repeats approximately every 20,000 bits,
theoretically exposing the user to differential attacks. Due
to its ease of use and quite effective security, Level 1 is the
default security level.
Level 2
Security Level 2 offers much greater encryption strength,
at the cost of slightly less intuitive operation. In Level 2,
the scrambling sequence never repeats (i.e. the PRNG is
free-running), so the receiver must be on and ready to
receive when the transmitter is first switched on. Some
signal loss is tolerated but if the transmitter should wander
out of range for more than ten seconds, it will be neces
sary to switch it off and on again to restart the sequence,
resynchronizing with the receiver. Security in this mode is
a great deal stronger than Level 1, since the scrambling
sequence never repeats. Only if the sequence is deliber
ately reused (i.e. by cycling transmitter power after
prolonged signal loss, or by reusing the same key session
after session) is a differential attack possible even in
theory.
Level 3
Security Level 3 offers the strongest encryption of all,
again at the cost of some convenience. Level 3 is much
like Level 2, except that the equipment itself enforces a
policy that
no portion of any scrambling sequence shall
ever be used more than once. This is a fundamental tenet
of cryptography: key reuse leads to vulnerability. Thus,
Level 3 security is about as close to the holy grail of the
one-time pad as any wireless vendor is likely to offer at a
reasonable price. Operation is a little different in Level 3:
1. The transmitter will not send any audio until a new key
is transferred from the receiver.
2. Only one transmitter may receive each key.
3. If the transmitter is out of range of the receiver for more
than ten seconds, it will be necessary to generate a
new key in order to continue using the system.
All three levels offer strong encryption, so each user may
make a policy decision based on an assessment of risk.
Those requiring ease of use may relax, knowing that
eavesdropping is extremely difficult even in Level 1. Many
users may find Level 2 to be just as convenient, allowing
them to use greater encryption strength. Those users
willing to follow stricter security procedures can use Level
3, the strongest encryption available today from a wireless
microphone.
ENCRYPTION KEY CREATION PROCESSOR FROM RECEIVER
RANDOM
BUTTON
PRESSES
AUDIO
INPUT
24-BIT
A/D CONVERTER
HIGH ENTROPY
ENCODER
(DIGITAL COMPRESSION)
ENCRYPTER
ENTROPY
HARVESTER
PRNG
128-BIT KEY
(SEED)
BIT STREAM
BIT STREAM
BIT STREAM
(SCRAMBLING SEQUENCE)
MODULATOR
OUTPUT SECTION
ANTENNA
DIGITAL TRANSMITTER HARDWARE
Rio Rancho, NM
9
