8e6 Technologies Enterprise Filter Authentication R3000 User Manual
Page 37
C
HAPTER
1: I
NTRODUCTION
F
ILTERING
E
LEMENTS
8
E
6 T
ECHNOLOGIES
, R3000 I
NTERNET
F
ILTER
A
UTHENTICATION
U
SER
G
UIDE
23
8. A lock profile takes precedence over all filtering profiles.
This profile is set up under Filter Options, by enabling the
X Strikes Blocking feature.
NOTE: A Threat Analysis Reporter (TAR) profile is another type
of lock profile that is weighted the same as a lock profile in the
precedence hierarchy.
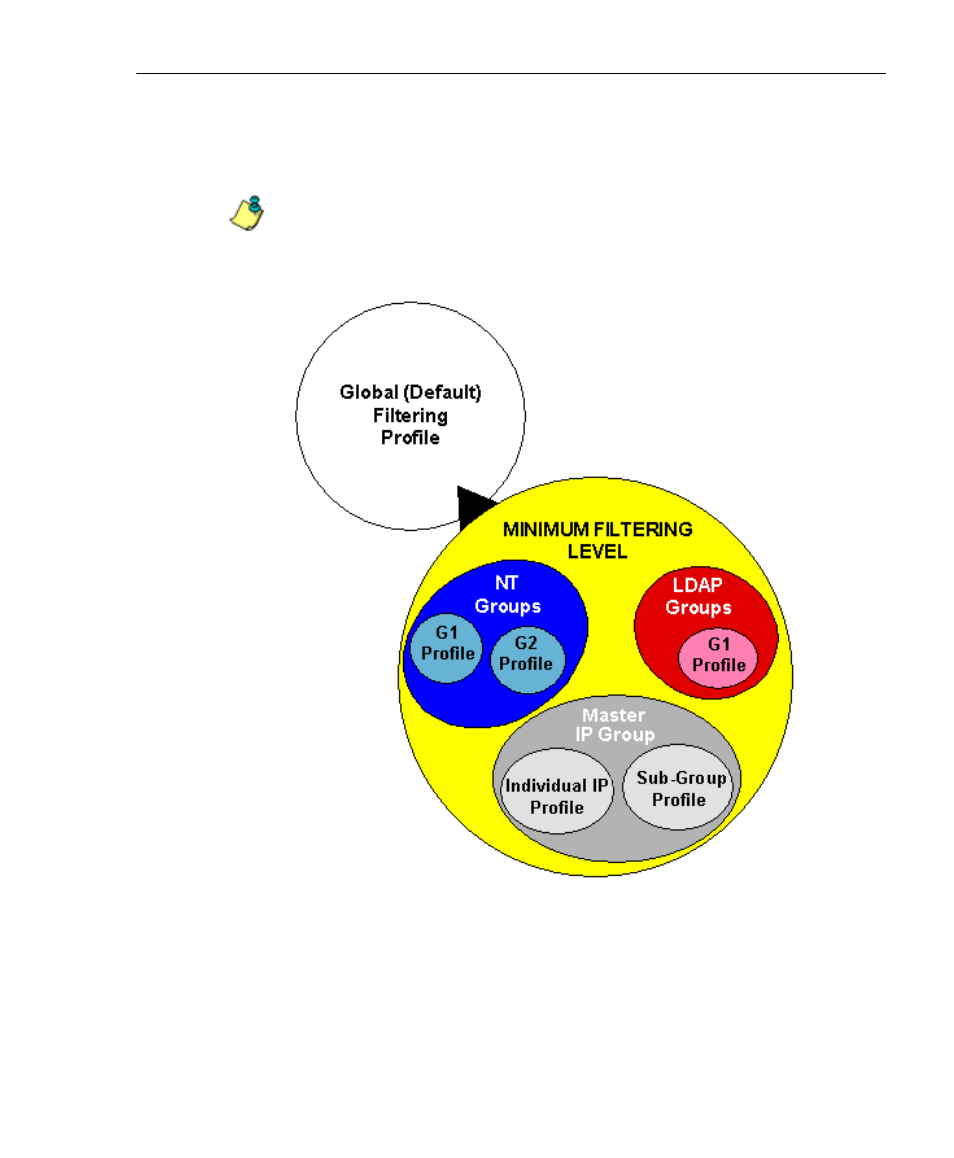
Fig. 1-4 Sample filtering hierarchy diagram
