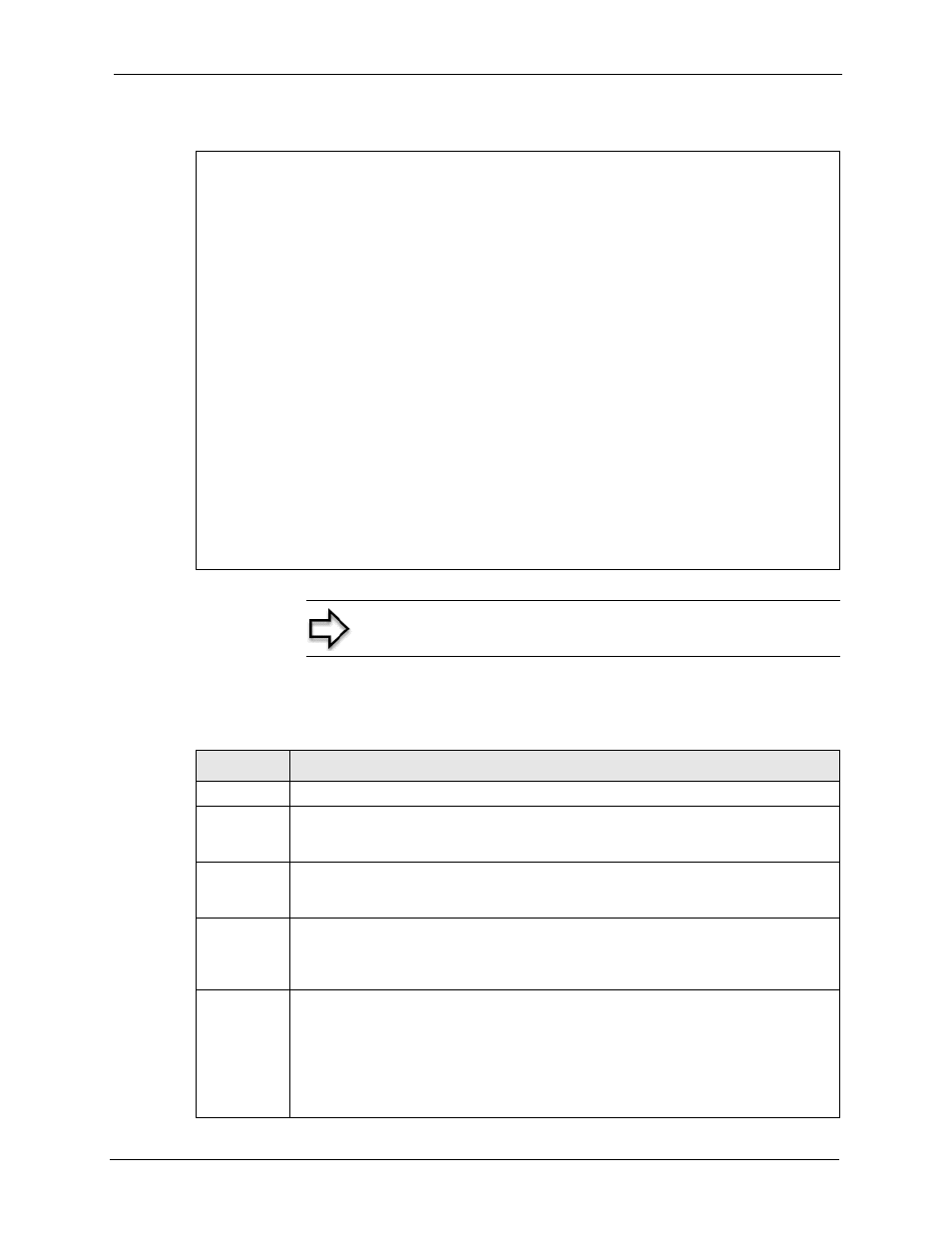
Figure 363 menu 27.1.1: ipsec setup, Table 208 menu 27.1.1: ipsec setup – ZyXEL Communications ZyXEL ZyWALL 35 User Manual
Page 565
ZyWALL 35 User’s Guide
Chapter 44 VPN/IPSec Setup
563
Figure 363 Menu 27.1.1: IPSec Setup
The following table describes the fields in this screen.
Menu 27.1.1 - IPSec Setup
Index= 1 Name= Taiwan
Active= Yes Keep Alive= No NAT Traversal= No
Local ID type = IP Content:
My Addr Type= IP Address= 0.0.0.0
Peer ID type= IP Content:
Secure Gateway Address= zwtest.zyxel.com.tw
Protocol= 0 DNS Server= 0.0.0.0
Local:
Addr Type= RANGE
IP Addr Start= 192.168.1.35 End/Subnet Mask=
192.168.1.38
Port Start= 0 End= N/A
Remote:
Addr Type= SUBNET
IP Addr Start= 4.4.4.4 End/Subnet Mask=
255.255.0.0
Port Start= 0 End= N/A
Enable Replay Detection = No
Key Management= IKE
Edit Key Management Setup= No
Press ENTER to Confirm or ESC to Cancel:
Note: You must also configure menu 27.1.1.1 or menu 27.1.1.2
to fully configure and use a VPN.
Table 208 Menu 27.1.1: IPSec Setup
FIELD
DESCRIPTION
Index
This is the VPN rule index number you selected in the previous menu.
Name
Enter a unique identification name for this VPN rule. The name may be up to 32
characters long but only 10 characters will be displayed in Menu 27.1 - IPSec
Summary.
Active
Press [SPACE BAR] to choose either Yes or No. Choose Yes and press [ENTER] to
activate the VPN tunnel. This field determines whether a VPN rule is applied before a
packet leaves the firewall.
Keep Alive
Press [SPACE BAR] to choose either Yes or No. Choose Yes and press [ENTER] to
have the ZyWALL automatically re-initiate the SA after the SA lifetime times out, even if
there is no traffic. The remote IPSec router must also have keep alive enabled in order
for this feature to work.
NAT
Traversal
Choose Yes and press [ENTER] to enable NAT traversal. NAT traversal allows you to
set up a VPN connection when there are NAT routers between the two IPSec routers.
The remote IPSec router must also have NAT traversal enabled. You can use NAT
traversal with ESP protocol using Transport or Tunnel mode, but not with AH protocol
nor with Manual key management.
In order for an IPSec router behind a NAT router to receive an initiating IPSec packet,
set the NAT router to forward UDP port 500 to the IPSec router behind the NAT router.
