Motorola S2500 User Manual
Page 13
MNR S2500 Security Policy
Version 1.2, Revision Date: 8/8/2008
Page
13
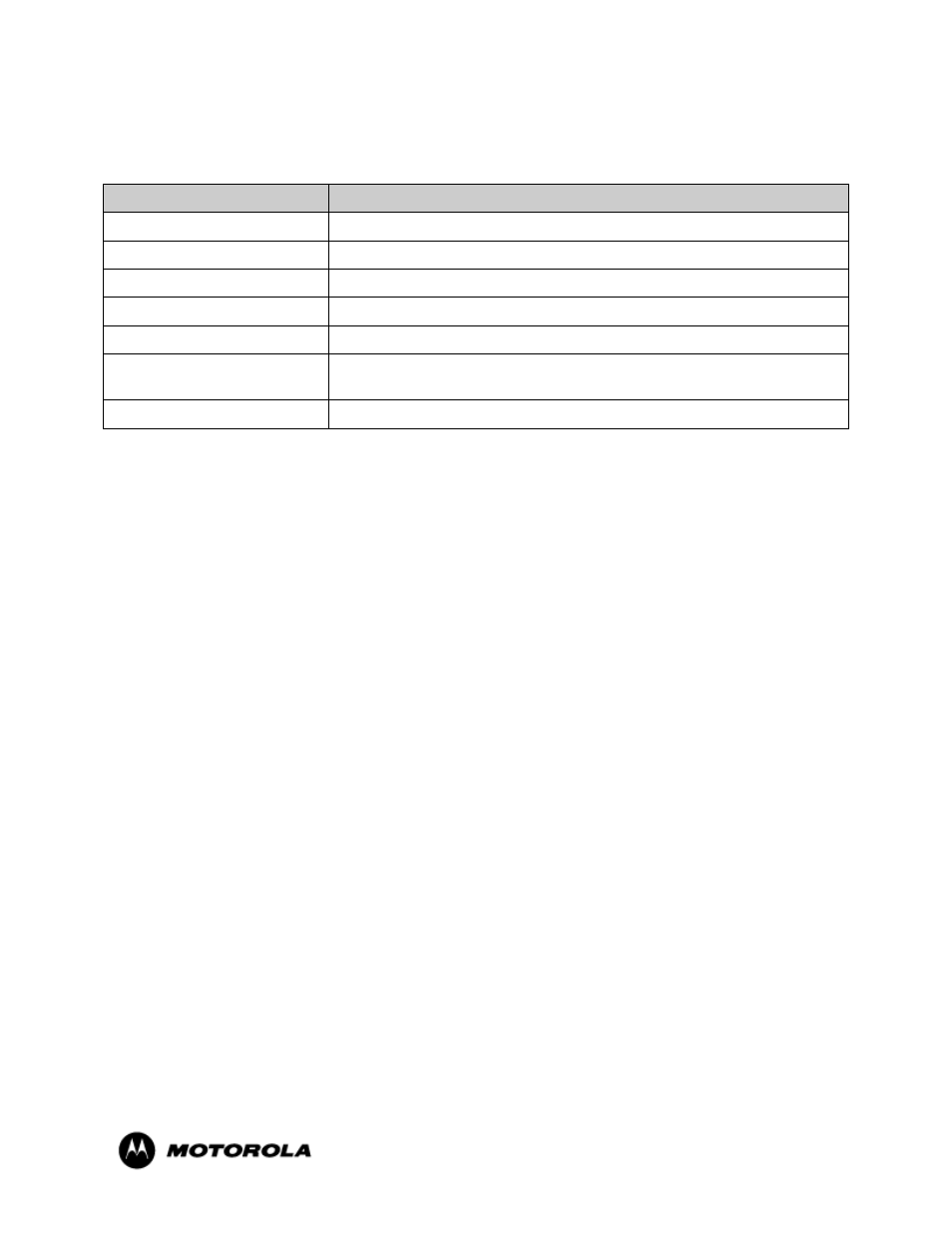
Definition of Public Keys:
The following public keys are contained within the module:
Key
Description/Usage
RSA Firmware Load Key
Distributed to module, for firmware authentication
SSH-RSA Key
Distributed to peer, used for SSH authentication
SSH-DSA Key
Distributed to peer, used for SSH authentication
SSH Known Host Keys
Distributed to module, used to authenticate peer
IKE DH public key (g^a)
Generated for IKE Phase 1 key establishment
IKE DH phase-2 public (g^a)
key
Phase 2 Diffie Hellman public keys used in PFS for key renewal (if
configured)
SSH DH Key
Generated for SSH key establishment
Table 9 – Public Keys
Definition of CSPs Modes of Access
Table 10 defines the relationship between access to CSPs and the different module services. The
modes of access shown in the table are defined as follows:
• Read: the data item is read from memory.
• Write: the data item is written into memory.
• Zeroize: the data item is actively overwritten.
- SB5101U DOCSIS 2.0 Cable Modem (16 pages)
- PTP 500 (20 pages)
- Netopia 3347-02-ENT (3 pages)
- SBV5220 (64 pages)
- AP-51XX (698 pages)
- SURFboard SVG2501 Series (34 pages)
- MESH Wireless Router MWR6300 (2 pages)
- MVME712AM (74 pages)
- SURFBOARD SBG1000 (16 pages)
- RSGu3502 (5 pages)
- SURFboard SBG941U (78 pages)
- Netopia 2240N-VGx (5 pages)
- SURFboard SVG2501 (8 pages)
- WR850G (93 pages)
- WR850GP (95 pages)
- USBW 200 (12 pages)
- ONCE SC140 (28 pages)
- Netopia 3300 (368 pages)
- MPC8260 (1006 pages)
- WNS25 (2 pages)
- Netopia 7000 (254 pages)
- Viadux 2000 Subscriber Bridge RC2010 (1 page)
- MVME5100 Series (5 pages)
- ColdFire MCF5282 (766 pages)
- MC9S12C-Family (136 pages)
- CG4500 (36 pages)
- SBG900 (130 pages)
- SURFBOARD SB5100 (2 pages)
- SURFboard SB6180 (20 pages)
- SURFBOARD SBG900 (16 pages)
- SURFboard SVG1501U (83 pages)
- SB5100 (74 pages)
- T3 (2 pages)
- H375 (5 pages)
- NETOPIA 2247/57-62 (22 pages)
- SBV5120 (56 pages)
- SBV5120 (57 pages)
- RG2200 (88 pages)
- CME-12B/BC (18 pages)
- SURFboard 574823-001-a (2 pages)
- SURFboard Cable Modem (66 pages)
- CME-12D60 (19 pages)
- DIGITAL VOICE MODEM SBV5122 (24 pages)
- SB4000 (2 pages)
- Canopy FSK and OFDM radios PTP 200 (OFDM (56 pages)
