Configuration - encryption – Asus USB-N66 User Manual
Page 15
USB-N66 WLAN Adapter User Manual
1
ASUS WLAN adapter
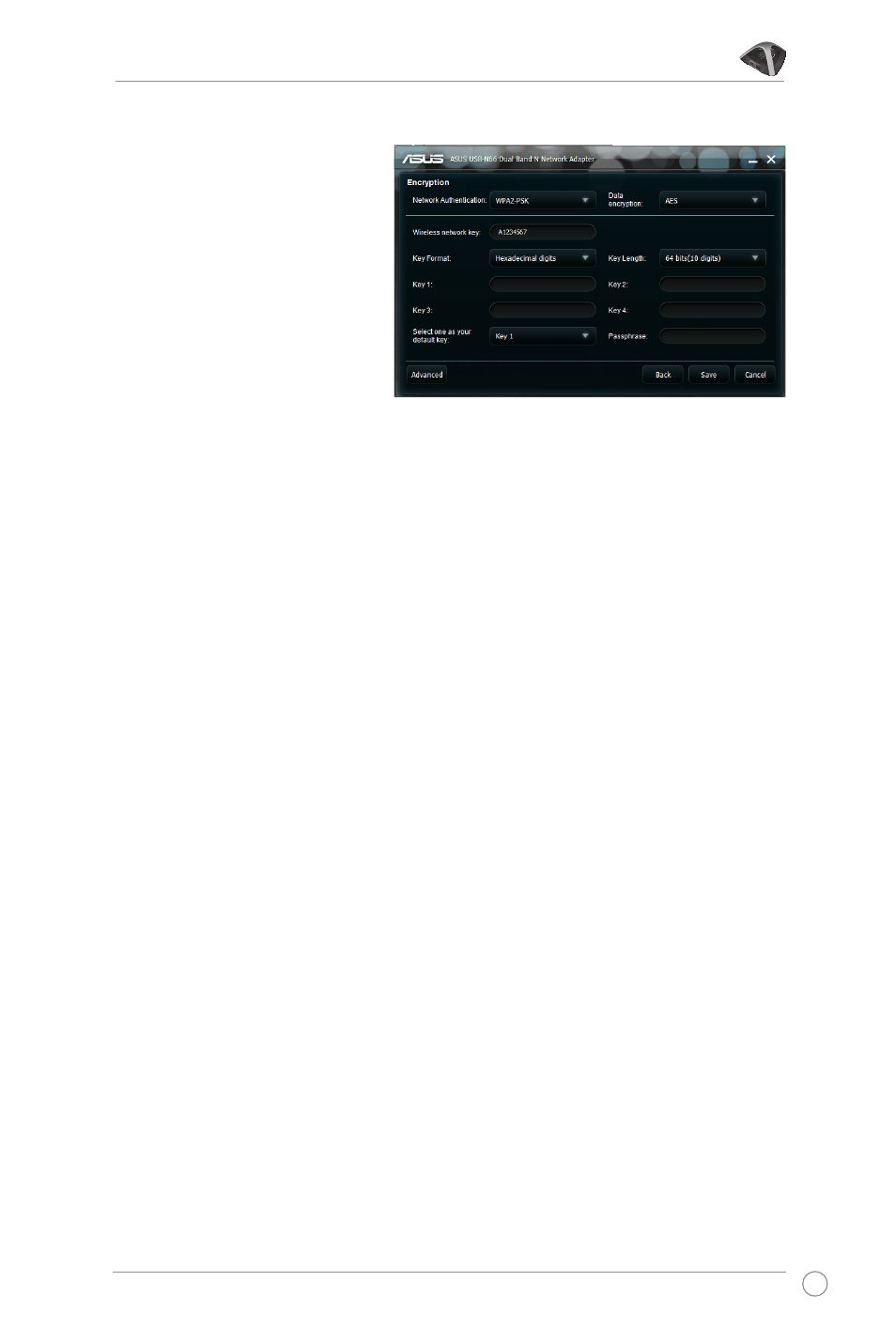
Configuration - Encryption
The Encryption page
allows you to set up the
encryption settings for your
WLAN adapter. For data
confidentiality in a wireless
environment, IEEE 802.11
specifies a Wired Equivalent
Privacy (WEP) algorithm to
offer transmission privacy
similar to wired network. WEP
uses keys to encrypt data
packets sent and decrypt
data packets received. The
encryption process can scramble frame bits to avoid disclosure to others. Wi-Fi
Protected Access (WPA) is an improved security system for 802.11 that encrypts
data sent over radio waves. WPA is developed to overcome the weakness of the
WEP protocol.
• Network Authentication - Set up authentication for your WLAN adapter.
Options are:
• Open - Sets the network operating in the Open System mode that
disables authentication protection for the network or use the WEP
encryption for the network.
• Shared - Sets the network operating in the Shared Key mode that uses
the WEP encryption for your network.
• WPA-Personal/WPA2-Personal - Use the WPA Pre-Shared Key/WPA2
Pre-Shared Key in the Infrastructure mode for authentication.
• WPA/WPA2-Enterprise/WEP 802.1X - Set these authentication modes
in the Infrastructure mode (needs to add a RADIUS server to confirm
the user’s identity). Two Extensible Authentication Protocol (EAP) are
supported In the RADIUS environment, including PEAP and TLS/Smart
Card.
• Data Encryption - Encrypts the data before it is transmitted over the air.
In the Open and Shared authentication modes, options are Disabled and
WEP.
• Disabled - Disables the encryption protection for your WLAN adapter.
• WEP - When you select this option, the cursor appears in the field for
Key 1. Key in 10 hexadecimal digits (0~9, a~f, and A~F) for the 64-bit
encryption.
In the WPA-PSK and WPA-Personal and WPA2-Personal authentication
and WPA-Personal and WPA2-Personal authentication
WPA-Personal and WPA2-Personal authentication
modes, options are: Temporal Key Integrity Protocol (TKIP) and Advanced
Encryption Standard (AES).
• TKIP - Dynamically generates unique keys to encrypt data packet.
• AES - Offers stronger protection and increases the complexity of
