Config - encryption, Chapter 3 - software reference – Asus WL-160N User Manual
Page 19
ASUS WLAN Adapter
1
Chapter 3 - Software Reference
Chapter 3
So
ftw
ar
e
Re
fe
re
nc
e
Network Authentication
Since there is no precise bound in
wireless LANs, the WLAN users need
to implement certain mechanism
to provide security solution. The
Authentication policies in this tab
provide protection of different levels
such as Open, Shared, WPA-PSK,
WPA, WPA2 and WPA2-PSK.
Open - Select this option to make the
network operate on Open System
mode, which use no authentication algorithm. Open stations and APs can
authenticate with each other without checking any WEP Key, even if there is.
Shared - Select this option to make the network operate on Shared key mode.
In a Share Key Authentication system, four-step exchange of frames is required
to validate that the station is using the same WEP Key as the access point.
WPA-PSK/ WPA2-PSK - Select this option to enable WPA Pre-Shared Key
under Infrastructure mode. It enables communication between your client and
APs using WPA-PSK/WPA2-PSK encryption mode.
WPA/ WPA2 - The network is operating in IEEE 802.1x authentication mode.
This mode is for environments with RADIUS (Remote Access Dial-in User
Service). In a RADIUS environment, five Extensible Authentication Protocol
(EAP) are supported, including PEAP, TLS/Smart Card, TTLS, LEAP and Md5-
Challenge.
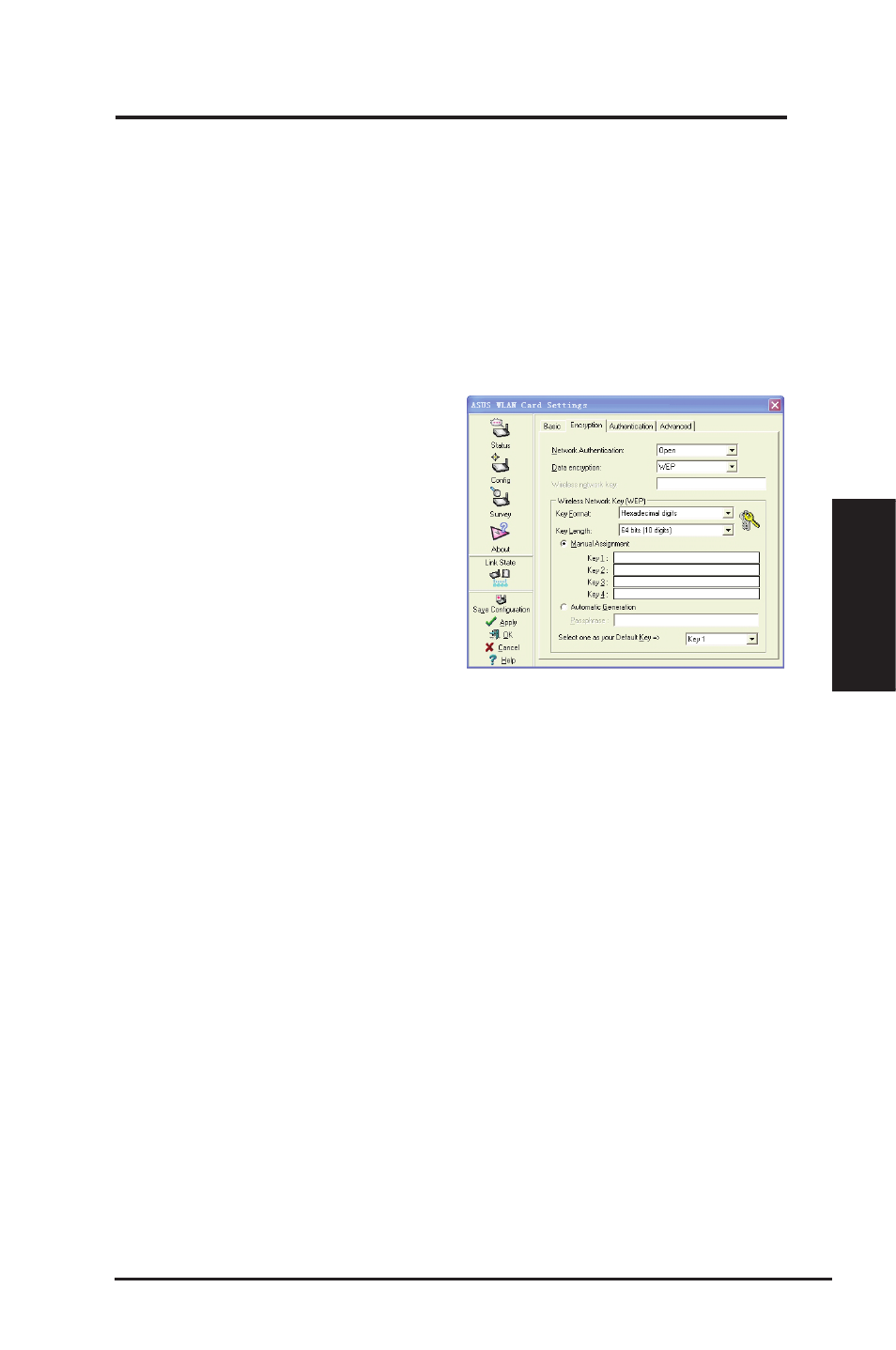
Config - Encryption
This page enables you to configure the Wireless LAN Adapter encryption
settings. For data confidentiality in a wireless environment, IEEE 802.11
specifies a Wired Equivalent Privacy (WEP) algorithm to offer transmission
privacy. The WEP uses keys to encrypt and decrypt data packets. The
encryption process can scramble frame bits to avoid disclosure to others. The
WPA/WPA2 is improved security system for 802.11 which are developed to
overcome the weakness of the WEP protocol.
