Authentication and security – Asus WL-530g User Manual
Page 9
English
ASUS Pocket Wireless Router
9
Quick Setup
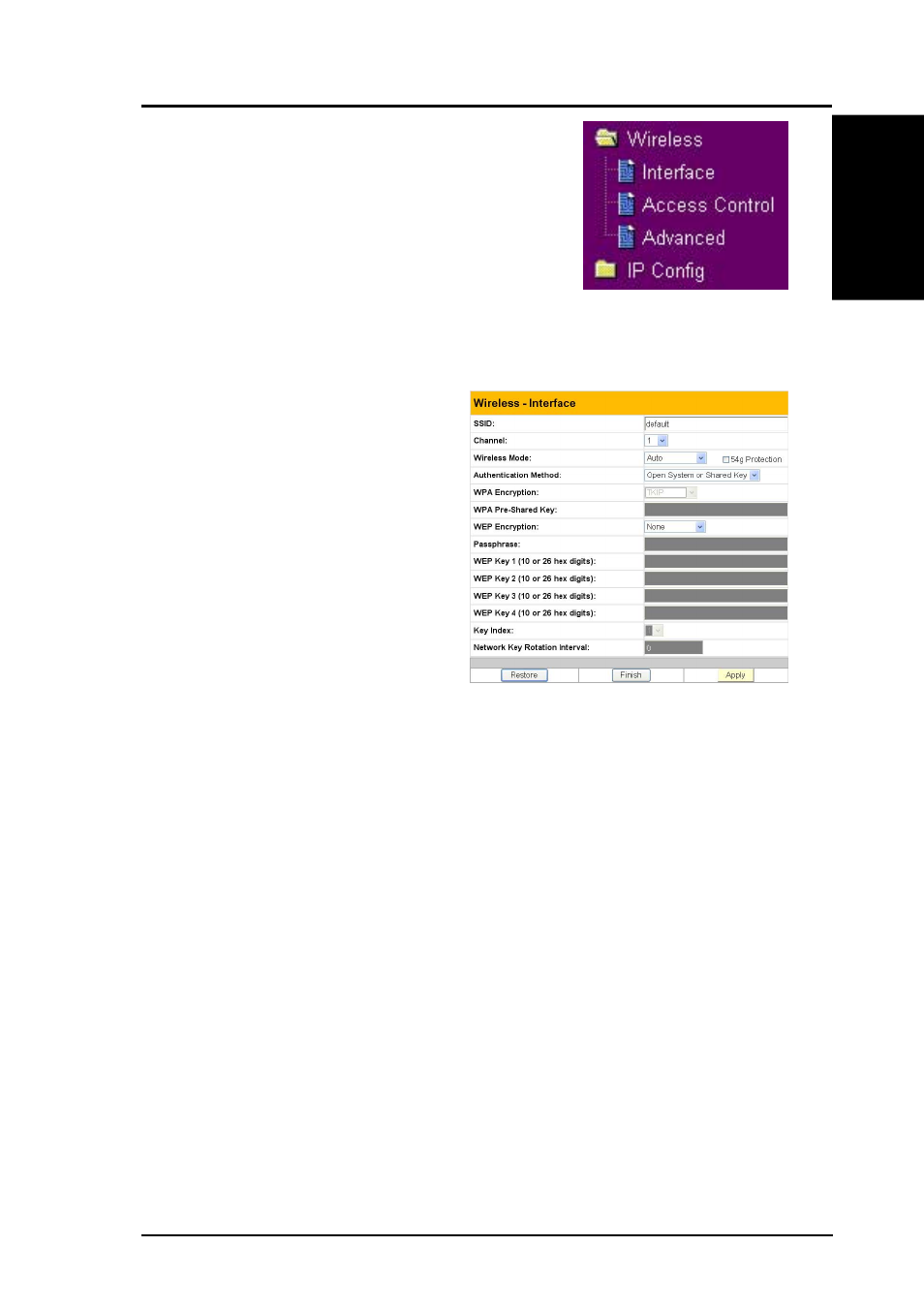
Authentication and Security
Click Wireless on the menu to reveal a submenu.
This field enables you to set different
authentication methods which determine
different encryption schemes. If all your clients
support WPA, using “WPA-PSK” is
recommended for better security.
WPA Encryption
When “WPA-PSK” authentication
method is used, the newly proposed
TKIP (Temporal Key Integrity
Protocol) encryption schemes are
applied.
TKIP: TKIP uses an encryption
algorithm, which is more stringent
than the WEP algorithm and also uses
existing WLAN calculation facilities
to perform encryption operations.
TKIP verifies the security
configuration after the encryption keys are determined.
WPA Pre-Shared Key
Selecting “TKIP” in the WPA Encryption, this field is used as a password
to begin the encryption process. Note: 8 to 63 characters are required.
- Xonar DX (80 pages)
- Xonar DX (10 pages)
- PCI Express Audio Card Xonar DX (70 pages)
- D2X (88 pages)
- Audio Card Xonar D2X (70 pages)
- Xonar D2X (88 pages)
- Xonar D2X (84 pages)
- ROG Xonar Phoebus (72 pages)
- ROG Xonar Phoebus (122 pages)
- Xonar DSX (26 pages)
- Xonar DSX (29 pages)
- Xonar DGX (58 pages)
- Xonar DGX (38 pages)
- Xonar DGX (33 pages)
- Xonar DG (54 pages)
- Xonar DG (58 pages)
- Xonar DG (32 pages)
- Xonar DG (28 pages)
- Xonar Essence ST (52 pages)
- Xonar Essence ST (35 pages)
- Xonar Essence ST (40 pages)
- Xonar Essence ST (53 pages)
- Xonar DS (54 pages)
- Xonar DS (33 pages)
- Xonar Xense (45 pages)
- Xonar Xense (47 pages)
- Xonar Xense (70 pages)
- Xonar U3 (56 pages)
- Xonar U3 (38 pages)
- Xonar Essence STX (32 pages)
- Xonar Essence STX (49 pages)
- Xonar Essence STX (10 pages)
- XONAR D1 E4009 (72 pages)
- Xonar D1 (72 pages)
- Xonar D1 (80 pages)
- Xonar D1 (10 pages)
- Xonar Essence One (5 pages)
- Xonar Essence One (7 pages)
- Xonar HDAV 1.3 (100 pages)
- Motherboard M4A78-EM (64 pages)
- A7N8X-VM/400 (64 pages)
- K8V-XE (86 pages)
- K8V-XE (20 pages)
- M2R32-MVP (160 pages)
- M2R32-MVP (60 pages)
